哈Ha!我是Swordfish Security的信息安全顾问,负责为我们的客户构建安全的DevOps。我顺应全球公司向DevSecOps的发展趋势,我尝试向讲俄语的社区传播最有趣的做法,并帮助我们的团队与客户一起建立此流程。在过去的两年中,DevSecOps越来越受到关注。新工具没有时间成为快速增长的实践中的一部分,这使我想以某种工具清单的形式放置某种检查点。起点是文章的发布Mail.ru的同事,其中突出显示了有关Kubernetes安全的部分。我决定扩展此列表,以涵盖SDLC生命周期的其他阶段,并提供一些新工具。

实践意味着可以在SDLC / DevOps的一个阶段中构建一套措施(威胁建模,SAST,DAST,SCA,Docker图像扫描,Kubernetes扫描,AWS Audit等)。
目录
开发人员
威胁建模
静态应用程序漏洞分析(SAST)
检查开源组件-SCA
寻找秘密
动态应用程序漏洞分析(DAST)
行为驱动开发测试
扫描Docker映像
行动
Kubernetes安全
漏洞管理
公共云安全
这还不是全部吗?
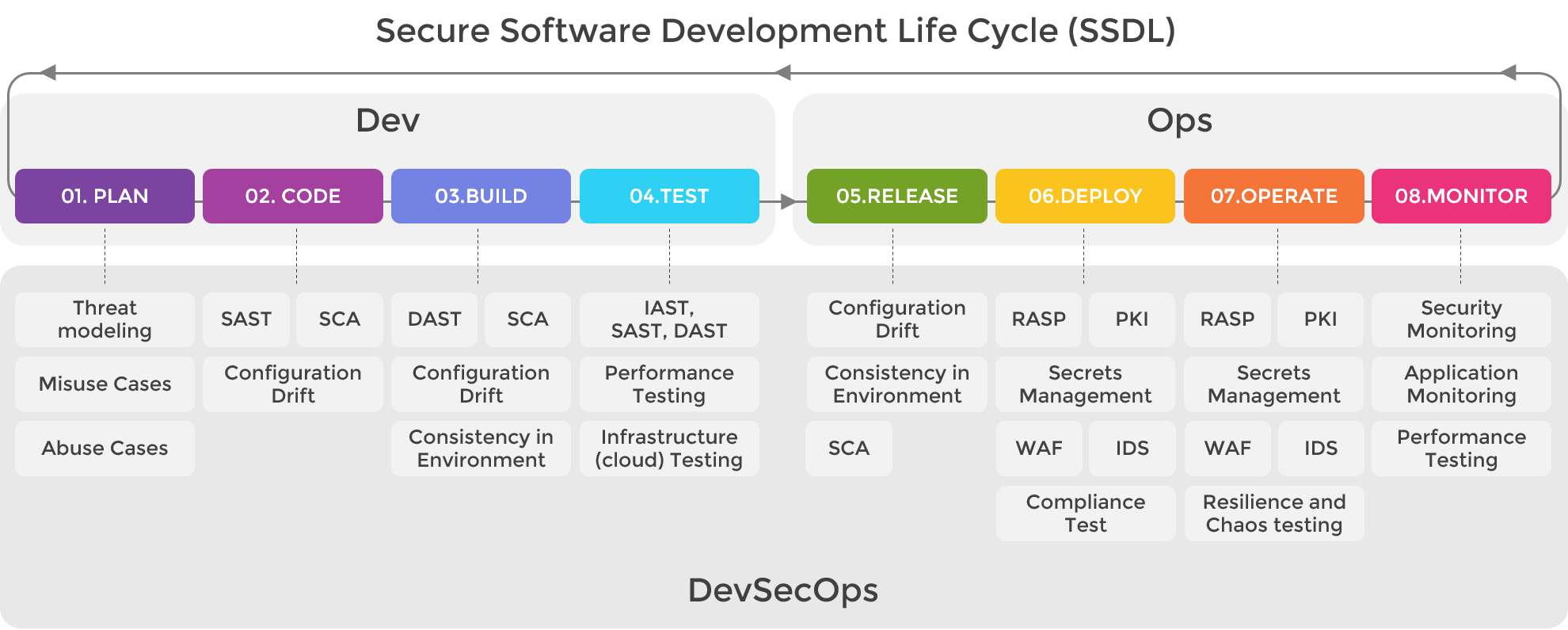
开发人员
威胁建模
Secure Development Lifecycle . , . , backlog. , , DevSecOps “Shift security to the left”.
IT-, . open-source , .
OWASP Threat Dragon
OWASP Threat Dragon
. , , STRIDE. , , , . GitHub.
Pytm
Pytm
Pytm - Python .
Pytm , . .
Materialize threats tool
Materialize threats tool
Materialize-threats - Python, draw.io , SQL . Gherkin.
open-source , , Enterpise- Irius Risks.
:
.drawio, data flow
, Rapid Threat Model Prototyping methodology( readme )
.drawio
materialize.py .drawio
Gherkin.
.
open-source :
Threatspec
Raindance
Microsoft Threat Modeling Tool
, , , , :
Awesome threat modeling
(SAST):
, . . Open-source , , , - . :
OWASP Source Code Analysis Tools
Static Analysis Tools
, .
Salus
Salus
, , Bandit, Gosec, Brakeman, open-source (Ruby,Node.js, Python,Go). :
# Navigate to the root directory of the project you want to run Salus on
$ cd /path/to/repo
# Run the following line while in the root directory (No edits necessary)
$ docker run --rm -t -v $(pwd):/home/repo coinbase/salusJSON/YAML . GitHub CircleCI.
ShiftLeft Scan
ShiftLeft Scan
Salus, . , docker (gosec, find-sec-bugs, psalm, bandit, …). Docker terraform, bash, kubernetes .
Python :
$ docker run --rm -e "WORKSPACE=${PWD}" -v "$PWD:/app" shiftleft/sast-scan scan --src /app --type python, IDE.
GitLab SAST
SAST GitLab
Gitlab DevOps , , open-source SAST, . Gitlab SCA, , fuzzing DevSecOps, Gold-.
LGTM
LGTM
LGTM - Semmle, GitHub. Semmle CodeQL, GitHub - Satellite.
Semgrep
Semgrep
, . , , AST Data flow, . , :
$ semgrep --config=<path/to/config> path/to/srcsemgrep :
rules:
- id: user-eval
patterns:
- pattern-inside: |
def $F(...):
...
- pattern-either:
- pattern: eval(..., request.$W.get(...), ...)
- pattern: |
$V = request.$W.get(...)
...
eval(..., $V, ...)
- pattern: eval(..., request.$W(...), ...)
- pattern: |
$V = request.$W(...)
...
eval(..., $V, ...)
- pattern: eval(..., request.$W[...], ...)
- pattern: |
$V = request.$W[...]
...
eval(..., $V, ...)Semgrep , ( , semgrep ):
. , open-source , SAST, . CWE , - . , , CWE CVE.
open-source - SCA
, , open-source, . ( , Equifax). , SCA , , .
Dependency Check
Dependency Check
Dependency Check - open-source OWASP . , , . , Secure SDLC . Dependency Check , , , , Dependency Track.
# Dependency Check Maven Plugin example
$ mvn org.owasp:dependency-check-maven:checkDependency Track
Dependency Track
Dependency Track - OWASP, -, Software bill of materials (SBOM) CycloneDx. Dependency Track BOM, , , NVD. Slack, Microsoft Teams, .
# CycloneDx Maven Plugin example to make SBOM
$ mvn org.cyclonedx:cyclonedx-maven-plugin:makeAggregateBomSnyk Open-source
Snyk Open-source
Snyk , open-source , SaaS-. (GitHub, Bitbucket), CLI.
snyk npm:
$ npm install -g snyk
$ snyk auth
$ snyk monitorSonatype Open-source
NVD ( ) Sonatype OSS, Sonatype, Nexus IQ. , , Nexus IQ SCA . Sonatype OSS - , Dependency Check Dependency Track. , Sonatype open-source SCA, Sonatype OSS:
Nexus Vulnerability Scanner - Sonatype
AuditJS - JS (NPM, Angular, yarn, bower)
Nancy - Golang
Jake - Conda
Chelsea - Ruby
Cheque - C/C++ (GCC)
Ahab - apt, apk, yum, dnf
Pants - Rust (Cargo)
Sonatype Depshield - GitHub
SCA:
SCA OWASP
ClearlyDefined
Renovate - White Source
Dependabot - GitHub open-source GitHub
, open-source , , , . , , . , . , .
git-secrets
git-secrets
$ git secrets --scan /path/to/fileGitrob
gitrob
$ export GITROB_ACCESS_TOKEN=<TOKEN>
$ gitrob <target>Gitleaks
gitleaks
$ gitleaks --repo-path=<path to repo>
$ gitleaks --repo=<url of github>Github-action.
TruffleHog
TruffleHog
$ trufflehog [-h] [--json] [--regex] [--rules RULES]
[--entropy DO_ENTROPY] [--since_commit SINCE_COMMIT]
[--max_depth MAX_DEPTH]
git_urlTruffleHog - , , .
GitGuardian
GitGuardian
SaaS . on-prem . .
. Password Vault (HashiCorp Vault, conjur, …)
(DAST):
Arachni
Arachni
open-source , . Docker-, CLI -. , . CWE-.
Docker:
$ docker run -d \
-p 222:22 \
-p 7331:7331 \
-p 9292:9292 \
--name arachni \
arachni/arachni:latest, REST API 7331 json.
OWASP ZAP
OWASP ZAP
open-source , CI/CD. GUI, CLI docker-. .
# OWASP ZAP as a daemon
docker run -p 8090:8090 -i owasp/zap2docker-stable zap.sh -daemon -port 8090 -host 0.0.0.0
# OWASP ZAP runs for 1 minute and then waits for the passive scanning to complete before reporting the results.
docker run -t owasp/zap2docker-weekly zap-baseline.py -t https://www.example.comKubernetes-.
, . , Arachni 10 , ZAP , , , .
w3af
w3af
, (, 2012 (https://xakep.ru/2012/11/09/w3af-pentest/)), docker- CI/CD
, open-source Jenkins AWS, w3af.
docker:
$ git clone https://github.com/andresriancho/w3af.git
$ cd w3af/extras/docker/scripts/
$ sudo ./w3af_console_docker. -. .
, open-source enterprise, . DAST .
Behaviour Driven Development
Behavioral Driven Development (BDD) ( “ ”)- , Test Driven Development (TDD) (“ ”). , , , , . BDD - Gherkin.
, .
Gauntlt
Gauntlt
Guantlt - , Behavioral Driven Development. Arachni, nmap, sslyze, sqlmap Gherkin.
# nmap-simple.attack
Feature: simple nmap attack to check for open ports
Background:
Given "nmap" is installed
And the following profile:
| name | value |
| hostname | example.com |
Scenario: Check standard web ports
When I launch an "nmap" attack with:
"""
nmap -F <hostname>
"""
Then the output should match /80.tcp\s+open/
Then the output should not match:
"""
25\/tcp\s+open
""", Guantlt “” , .
. Guantlt BDD-Security, OWASP ZAP, Tenable Nessus Scanner.
Docker:
, Docker ( Docker DevOps), Docker- .
, , .
.
Clair
Clair
CVE . UI , Klar.
$ docker run -d -e POSTGRES_PASSWORD="" -p 5432:5432 postgres:9.6
$ docker run --net=host -d -p 6060-6061:6060-6061 -v $PWD/clair_config:/config quay.io/coreos/clair:latest -config=/config/config.yamlKlar
Klar
API Clair.
$ mkdir klar && cd klar && wget https://github.com/optiopay/klar/releases/download/v2.4.0/klar-2.4.0-linux-amd64 -O klar && chmod +x klar
$ CLAIR_ADDR=http: //localhost:6060 CLAIR_THRESHOLD=10 ./klar <docker image>Trivy
Trivy
Trivy ( Alpine, RedHat (EL), CentOS, Debian GNU, Ubuntu) (Gemfile.lock, Pipfile.lock, composer.lock, package-lock.json, yarn.lock, Cargo.lock) Clair , , .tar Docker .
# Download bin
$ wget https: //github.com/knqyf263/trivy/releases/download/v0.1.3/trivy_0.1.3_Linux-64bit.deb
$ dpkg -i ./trivy_0. 1 .3_Linux-64bit.deb
# Scan image
$ trivy bkimminich/juice-shop
# Scan image in tar
$ trivy -i ./ my_saved_docker_image.tarAnchore
Anchore
Docker. REST API CLI.
$ anchore-cli --u admin --p foobar image add httpd:latest
$ anchore-cli --u admin --p foobar image vuln httpd:latest allAquaMicroscanner
AquaMicroscanner
Aqua Security, Trivy.
$ docker run --rm -it aquasec/microscanner --register <email address>ADD https://get.aquasec.com/microscanner /
RUN chmod +x /microscanner
RUN /microscanner <TOKEN> [--continue-on-failure]. CVE :
Testing docker CVE scanners. Part 1: false negatives and what they mean for your security
Testing Docker CVE Scanners. Part 2: How good is package detection?
Testing docker CVE scanners. Part 2.5 — Exploiting CVE scanners
Testing Docker CVE scanners. Part 3: Test it yourself / Conclusions
Dagda
Dagda
Dagda , Dependency Check, Retire.js ClamAV .
$ export DAGDA_HOST='127.0.0.1'
$ export DAGDA_PORT=5000
$ python3 dagda.py vuln --init
$ python3 dagda.py check --docker_image jboss/wildflyDocker bench
Docker Bench
Docker bench - compliance- , .
CIS Benchmarks Docker.
$ docker run -it --net host --pid host --userns host --cap-add audit_control \
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
-v /etc:/etc:ro \
-v /usr/bin/containerd:/usr/bin/containerd:ro \
-v /usr/bin/runc:/usr/bin/runc:ro \
-v /usr/lib/systemd:/usr/lib/systemd:ro \
-v /var/lib:/var/lib:ro \
-v /var/run/docker.sock:/var/run/docker.sock:ro \
--label docker_bench_security \
docker/docker-bench-securityDockle
Dockle
compliance-, , CIS.
$ docker run --rm goodwithtech/dockle:v${DOCKLE_LATEST} [YOUR_IMAGE_NAME]Ops:
Kubernetes Security
Deploy. Kubernetes, Docker, Kubernetes , Kubernetes .
:
My Arsenal of Cloud Native (Security) Tools by MARCO LANCINI
Kube-bench
Kube-bench
( ) Aqua Security. CIS Kubernetes Benchmark Kubernetes ( GKE, EKS and AKS)
:
# Run inside a container
$ docker run --rm --pid=host \
-v $(which kubectl):/usr/bin/kubectl \
-t aquasec/kube-bench:latest <master|node>
# Run in a cluster - on master node
$ kubectl run \
--rm \
-it \
kube-bench-master \
--image=aquasec/kube-bench:latest \
--restart=Never \
--overrides="{ \"apiVersion\": \"v1\", \
\"spec\": { \"hostPID\": true, \
\"nodeSelector\": \
{ \"kubernetes.io/role\": \"master\" }, \
\"tolerations\": [ { \
\"key\": \"node-role.kubernetes.io/master\", \
\"operator\": \"Exists\", \
\"effect\": \"NoSchedule\" }]}}" \
-- master \
--version 1.8
# Run in a cluster - on worker nodes
$ kubectl run \
--rm \
-it \
kube-bench-node \
--image=aquasec/kube-bench:latest \
--restart=Never \
--overrides="{ \"apiVersion\": \"v1\", \
\"spec\": { \"hostPID\": true } }" \
-- node \
--version 1.8Kubernetes Auto Analyzer
Kubernetes Auto Analyzer
, Kube-bench, . Kube-bench Aqua Security.
# Put the config file in a directory and mount it to the /data folder
$ docker run --rm \
-v /data:/data raesene/kube_auto_analyzer \
-c /data/admin.conf -r testdock
# Provide a KUBECONFIG file to identify and authenticate the session
$ kubeautoanalyzer -c <kubeconfig_file_name> -r <report_name> --htmlKube-hunter
Kube-hunter
Kubernetes. , IP- / Kubernetes.
# Run from docker
$ docker run -it --rm --network host aquasec/kube-hunter
# Run from kubectl
$ kubectl run --rm -it \
kube-hunter \
--image=aquasec/kube-hunter \
--restart=Never \
--overrides="{ \"apiVersion\": \"v1\", \
\"spec\": { \"hostNetwork\": true } }"KubiScan
KubiScan
RBAC- Kubernetes.
, CyberARK.
# Run from MASTER node
$ docker run -it --rm -e CONF_PATH=~/.kube/config -v /:/tmp cyberark/kubiscan [CMD]
# Search for pods with privileged accounts
$ kubiscan -rp
# Show all risky subjects (users, service accounts, groups)
$ kubiscan -rs
# Show all the rules a service account has
$ kubiscan -aars "SANAME" -ns "default" -k "ServiceAccount"
# List service account RoleBindings
$ kubiscan -aarbs "SANAME" -ns "default" -k "ServiceAccount"Krane
Krane
, RBAC RBAC RedisGraph. RBAC . Krane CLI, docker- , CI/CD.
Statboard
Starboard
, Kubernetes CustomResourceDefinitions (CRDs) trivy, kube-bench, kube-hunter. Starboard kubectl- Octant, Kubernetes.
$ starboard find vulnerabilities deployment/nginx --namespace dev
$ starboard get vulnerabilities deployment/nginx \
--namespace dev \
--output yamlKubeaudit
Kubeaudit
, Kubernetes.
# Run from kubectl (as plugin)
$ kubectl audit allKubesec
Kubesec
Kubernetes .
$ krew install kubesec-scan
$ kubectl kubesec-scan pod <podname>Deepfence Runtime Threat Mapper
Deepfence Runtime Threat Mapper
community- . , , CI/CD , Registry. SIEM, Slack, Jira, Amazon S3 ( ).
Sysdig Falco
Sysdig Falco
run-time Sysdig, .
Vulnerability Management
SAST, DAST, SCA, Docker Kubernetes, . Vulnerability Management . , API - -. AppSec.Hub, , DevSecOps- CI/CD . open-source .
DefectDojo
DefectDojo
OWASP. (22+) open-source (ZAP, Trivy, nmap, Dependency Check), enterprise (Veracode, Checkmarx, Twistlock). , API.
.
Secure code Box
Secure code box
Open-source , (ZAP, NMAP, Nikto, Arachni), docker-compose Kibana Elasticsearch. DefectDojo, , ( issue ). UI. -.
, , one-button-click-solution .
Archery
Archery
open-source . Acuntetix, Nessus, Burp, Netsparker, WebInspect. DefectDojo, , ZAP, Burp OpenVAS. , false positive. CI/CD.
vulnerability management:
Faraday
VulnReport
Public Cloud Security
DevOps (AWS, GCP, Azure, Oracle) on-prem .
, . , , .
AWS-inventor
AWS-inventor
AWS AWS.
$ python aws_inventory.py
# Select the generated JSON file when prompted
$ firefox gui/dist/index.htmlAws-public-ips
AWS-puclic-ips
AWS ip-.
# Uses default ~/.aws/credentials
$ aws_public_ips -f json -s apigateway,cloudfront,ec2, \
elasticsearch,elb,elbv2,lightsail,rds,redshift
# With a custom profile
$ AWS_PROFILE=production aws_public_ips ...CloudSploit
CloudSploit
compliance- AWS, GCP, Azure, OCI. , CIS PCI DSS.
# Edit the index.js file with your AWS key and secret
# Run a standard scan
$ node index.js
# Run a compliance scan
$ node index.js --compliance=hipaaAWS Security Benchmark
AWS Security Benchmark
AWS CIS Amazon Web Services Foundations Benchmark 1.1.
$ python aws-cis-foundation-benchmark-checklist.pyS3 Scan
S3 Scan
, S3- .
$ python s3scan.py [-f <format>] [-p <profile>]. , AWS Security:
My-arsenal-of-aws-security-tools
G-Scout
G-Scout
, GCP.
# Permissions required on the projects: Viewer, Security Reviewer, Stackdriver Account Viewer
$ python gscout.py --project-id <projectID>ScoutSuite
ScoutSuite
GCP, AWS, Oracle, Azure.
# GCP example
# Using an user account
$ python Scout.py --provider gcp --user-account --project-id <projectID>
# Using a service account
$ python Scout.py --provider gcp \
--service-account --key-file service_account.json \
--project-id <projectID>?
, , DevOps/SDLC. , . , IaC. , . BSIMM OWASP SAMM.
, .
RASP - , , ( , , .). Container Run-time Security ( Sysdig Falco). RASP -:
OpenRASP
IAST - , SAST DAST:
Contrast
Fuzzing - , , :
Awesome Fuzzing
IaC Security - :
Cfn Nag - AWS CloudFormation
Checkov - Terraform, AWS CloudFormation Kubernetes
Terrascan - Terraform
Tfsec - Terraform AWS, Azure GCP.
Kubernetes YAML validating:
Kubeval
Kube-score
Config-lint
Copper
Conftest
Polaris
Compliance-as-code - :
Chef InSpec
Compliance Masonry
OpenSCAP
Security Chaos Engineering - , : "" , , , "" . , . - , . Security Chaos Engineering Chaos Engineering , . , , Security Groups, , , VPC, "" . , . :
ChaoSlingr
Security Monkey
Kube-monkey
DevSecOps :
DevSecOps Wine - DevSecOps
DevSecOps Wine Chat -
CloudSec Wine - Public Cloud Security
Mobile AppSec World -
DevSecOps
UPD.
, Awesome DevSecOps , :
Awesome DevSecOps