 头衔在说什么奖牌?我们正在基于公共密钥密码学标准(公共密钥密码学标准-PKCS)谈论公共密钥基础设施(Public Key Infrastructure-PKI / IEC)。)。公钥基础结构包括许多不同的对象和与其一起使用的机制,以及用于对象彼此交互的协议(例如TLS,OCSP)。 PKI / PKI对象包括x509证书和密钥对(私钥和公用密钥),签名和加密的文档(pkcs#7,CMS),用于存储私钥的安全容器(pkcs#8)和带有密钥的私钥证书(pkcs# 12)等该机制不仅包括允许您使用各种算法对文档进行加密和签名的加密功能,还包括根据标准(证书,请求,签名/加密的文档,协议包等)形成最终PKI对象的功能。 .P。)。是的,以及如何不记得中央PKI / PKI对象-认证中心(CA)。
头衔在说什么奖牌?我们正在基于公共密钥密码学标准(公共密钥密码学标准-PKCS)谈论公共密钥基础设施(Public Key Infrastructure-PKI / IEC)。)。公钥基础结构包括许多不同的对象和与其一起使用的机制,以及用于对象彼此交互的协议(例如TLS,OCSP)。 PKI / PKI对象包括x509证书和密钥对(私钥和公用密钥),签名和加密的文档(pkcs#7,CMS),用于存储私钥的安全容器(pkcs#8)和带有密钥的私钥证书(pkcs# 12)等该机制不仅包括允许您使用各种算法对文档进行加密和签名的加密功能,还包括根据标准(证书,请求,签名/加密的文档,协议包等)形成最终PKI对象的功能。 .P。)。是的,以及如何不记得中央PKI / PKI对象-认证中心(CA)。
任何Internet用户在不知不觉中都会使用各种PKI / PKI机制和对象,例如在访问各种站点时,在其工作流中签名和/或加密电子邮件或使用电子签名时使用HTTPS协议。
用于创建公钥基础结构的最先进的工具PKI / PKI软件工具是OpenSSL和网络安全服务(NSS)。
OpenSSL是一套完善的开源密码库和实用程序,支持几乎所有的低级哈希,加密和电子签名算法,并且还实现了大多数流行的密码标准,包括:允许您创建RSA,DH,DSA,EC密钥,问题X.509证书,加密和签名数据以及创建SSL / TLS连接。
应该注意的是,OpenSSL实用程序使用的对象存储在文件(证书,密钥)中。网络安全服务(NSS)是
一套完整的开放源代码加密库和实用程序。
OpenSSL与NSS之间的主要区别在于,OpenSSL假定证书和密钥存储在文件中,而NSS使用PKCS#11数据库和令牌存储证书和密钥。
最重要的是,两个项目(OpenSSL和NSS)都严格遵守标准,因此在不同项目中一起使用时没有问题。当站点/门户网站是基于Apache和基于OpenSSL的mod_ssl基于Apache构建站点/门户时,例如通过支持TLS 1.0 / TLS 1.2和TLS 1.3的Firefox进行访问时,可以很好地利用它们的联邦优势。使用NSS库执行。
下面将显示如何使用OpenSSL和NSS实用程序解决相同的问题。将来,每个人都可以使用自己喜欢的实用程序。
通过查看该实用程序的源代码,任何人都可以熟悉该库的功能。
查看文件中存储的证书和其他实体
OpenSSL软件包中有一个实用程序-openssl,其第一个参数是命令本身(标准命令),必须执行该命令:
$ openssl帮助
Standard commands
asn1parse ca ciphers cms
crl crl2pkcs7 dgst dhparam
dsa dsaparam ec ecparam
enc engine errstr exit
gendsa genpkey genrsa help
list nseq ocsp passwd
pkcs12 pkcs7 pkcs8 pkey
pkeyparam pkeyutl prime rand
rehash req rsa rsautl
s_client s_server s_time sess_id
smime speed spkac srp
ts verify version x509
Message Digest commands (see the `dgst' command for more details)
blake2b512 blake2s256 gost md2
md4 md5 rmd160 sha1
sha224 sha256 sha384 sha512
Cipher commands (see the `enc' command for more details)
aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb
aes-256-cbc aes-256-ecb base64 bf
bf-cbc bf-cfb bf-ecb bf-ofb
camellia-128-cbc camellia-128-ecb camellia-192-cbc camellia-192-ecb
camellia-256-cbc camellia-256-ecb cast cast-cbc
cast5-cbc cast5-cfb cast5-ecb cast5-ofb
des des-cbc des-cfb des-ecb
des-ede des-ede-cbc des-ede-cfb des-ede-ofb
des-ede3 des-ede3-cbc des-ede3-cfb des-ede3-ofb
des-ofb des3 desx idea
idea-cbc idea-cfb idea-ecb idea-ofb
rc2 rc2-40-cbc rc2-64-cbc rc2-cbc
rc2-cfb rc2-ecb rc2-ofb rc4
rc4-40 rc5 rc5-cbc rc5-cfb
rc5-ecb rc5-ofb seed seed-cbc
seed-cfb seed-ecb seed-ofb zlib
$
如您所见,当执行openssl help命令时,除了命令列表本身之外,还将显示受支持的哈希算法和加密算法的列表(它们的列表包括compression和base64函数)。
要查看证书(x509),请求(req)或证书吊销列表(crl),只需运行以下命令:
openssl x509 [| req | crl] [-nameopt utf8] -inform PEM | DER -noout -in <文件名> ...
例如,命令:
$openssl x509 -text -nameopt utf8 -inform PEM -noout -in cert.pem将在计算机屏幕上以技术形式(x509-文本)显示证书的内容,该证书形式存储在以PEM(base64)编码的cert.pem(-in cert.pem)文件中(-inform PEM),并且包含utf-8编码的字符(-nameopt utf8)。在这种情况下,PEM编码的证书本身将不会显示在屏幕上(-noout)。
在NSS软件包中,pp实用程序执行相同的操作。
pp实用程序是用于包含DER或PEM编码的ASN.1结构的文件的Pretty Print实用程序:
Usage: pp [-t type] [-a] [-i input] [-o output] [-w] [-u], - c-证书;
- cr-证书申请;
- pk-公钥;
- pk-公钥文件;
- crl-吊销证书列表。
请注意另一种适用于证书的类型ci(证书身份)。此类型使您可以从证书中获取标识信息,例如主题(所有者),发行者(发布者),序列号(序列号),指纹(SHA-1和SHA-256指纹)。 x509的openssl实用程序具有类似的参数。
默认情况下,所有对象均假定为DER编码。如果对象采用PEM编码,则必须指定“ -a”参数(类似于openssl实用程序的“ -inform PEM”参数)。如果对象包含UTF-8编码的字符,则设置另一个参数“ -u”。回想一下openssl实用程序具有类似的参数-“ -nameopt utf8”。
NSS软件包还包含一个用于查看对象的ASN.1-结构的实用程序,类似于openssl实用程序asn1.parse。这是derdump实用程序:
$derdump -i < > [-o < >]从实用程序的名称开始,它可以处理DER编码格式的文件。但是没关系。该软件包包括两个实用程序,可将文件从PEM / BASE64编码转换为DER编码,反之亦然。这些是atob和btoa实用程序。
例如,要在OpenSSL中将证书从PEM格式转换为DER格式,请运行以下命令:
$openssl x509 -inform der -in CERT.der -out CERT.pem 在NSS中,它看起来像这样:
$btoa -in CERT.der -out CERT.pem -w "CERTIFICATE"“ -w”选项指定在输出文件的开头和结尾包含哪些文本。在这种情况下,``-w证书''将导致PEM标准的OpenSSL标头和标尾:
-----BEGIN CERTIFICATE-----
< BASE64>
-----END CERTIFICATE----- OpenSSL和NSS都可以使用pkcs#12容器。而且它们不仅允许创建,而且还允许查看pkcs12容器的内容。但是,在使用openssl实用程序时,必须首先拆卸容器,并将容器中的证书保存在单独的文件中。之后,您可以安全地查看它们。在NSS中,查看容器中的内容可以一次完成。为此,请使用以下格式的pk12util实用程序:
pk12util -l < pkcs12> [-W < pkcs12>] [-d < NSS>] [-h <>]例如:
$ pk12util -l cert_RSA.p12 -W 01234567
Certificate(has private key):
Data:
Version: 3 (0x2)
Serial Number: 3 (0x3)
Signature Algorithm: PKCS #1 SHA-1 With RSA Encryption
Issuer: "CN=CA-RSA"
Validity:
Not Before: Thu May 21 09:50:00 2020
Not After : Fri May 21 16:17:00 2021
Subject: "CN=soft.lissi.ru"
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
a2:f3:e1:63:fd:4f:60:4e:a9:de:56:37:a6:be:54:f3:
3d:67:9a:68:9e:f1:47:69:e3:3a:10:b0:2e:88:0c:ef:
7c:7f:48:47:6b:c0:75:63:c7:13:23:88:9a:ff:9a:48:
30:6a:a0:52:53:6f:4e:e5:84:c0:a1:b0:50:a2:ab:3d:
f9:62:2c:d8:30:be:19:1b:c9:f4:b8:20:57:a1:8e:5e:
61:8c:a7:50:91:44:61:99:71:40:bb:dc:4c:b7:7c:67:
be:a0:71:26:9f:af:dd:69:63:84:7d:93:3f:92:1b:fb:
d1:78:d7:95:75:42:8e:14:a8:63:e2:7b:7d:ef:c8:74:
35:7c:39:44:82:ad:92:1f:98:0e:91:95:c8:d8:bd:41:
fc:44:7e:4d:f5:94:d1:cc:25:ea:df:69:d7:b1:d7:86:
ad:4d:03:f1:35:65:03:a6:84:f8:26:6e:9b:d3:c9:67:
d5:a5:a4:9e:c7:82:76:28:9f:90:14:f1:16:6a:29:5d:
f8:df:c6:6c:e4:21:0d:6f:c5:87:61:a0:65:e3:97:0f:
96:42:ad:7d:96:79:ef:1d:ab:6c:e3:a0:da:3a:65:d8:
39:69:f3:20:e2:b1:27:fe:cb:4c:8c:0c:f5:76:f2:65:
a0:c7:bb:08:b0:f5:50:c0:96:8a:30:e9:75:f7:56:65
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is not a CA.
Name: Certificate Key Usage
Usages: Digital Signature
Non-Repudiation
Key Encipherment
Name: Certificate Subject Alt Name
DNS name: "lissi.ru"
Name: Certificate Type
Data: <SSL Server>
Name: Certificate Comment
Comment: "xca certificate"
Signature Algorithm: PKCS #1 SHA-1 With RSA Encryption
Signature:
12:8c:c3:7e:e9:18:5a:d7:ee:f8:10:8b:72:55:ba:ee:
8b:85:6c:aa:e3:de:58:26:a2:da:15:c6:3b:15:d9:82:
6d:02:33:16:cc:0c:84:9d:96:b0:67:d4:63:10:b5:42:
a1:c3:de:cb:40:6f:9b:9b:eb:c1:98:b6:66:55:ae:88:
56:14:02:5c:62:8c:bc:22:97:94:cf:53:da:2e:47:c1:
c6:83:dc:39:6f:0b:b8:39:4e:66:89:a3:9d:51:c6:e3:
bd:fc:9e:f3:7b:02:a4:77:bc:08:4e:89:e6:57:54:5c:
c1:cc:83:93:9e:4e:f5:41:4e:b5:13:bc:64:29:a9:8d:
ce:13:ae:48:6c:21:fc:da:2a:a2:87:67:f8:df:23:53:
08:a3:11:93:69:91:84:40:4b:58:c1:f3:d0:78:dc:33:
f6:a5:a6:6f:ed:39:a9:ec:f3:48:e8:06:09:4c:c3:9f:
9c:0f:58:80:7f:f5:09:40:2a:f1:cf:42:d7:5b:57:62:
99:e7:dc:a5:31:f3:9d:1f:5a:88:c2:30:1b:8c:ec:69:
8b:87:dc:4c:08:9e:70:49:3d:5e:7b:8f:6f:98:50:8b:
0d:b9:8f:c1:7e:9b:1f:c2:76:3a:ca:c5:e3:3d:ea:93:
81:c0:3b:e2:b7:d1:5d:e4:fd:48:d6:1b:8f:96:e2:18
Fingerprint (SHA-256):
D3:38:99:C9:8B:A5:49:96:BC:26:7B:10:1E:2A:7C:4B:55:15:E5:94:47:C6:D0:49:44:2E:48:58:1B:CF:83:7E
Fingerprint (SHA1):
D5:26:80:B7:CE:40:5B:54:85:F6:B2:31:58:C3:3E:9D:A4:3D:C1:F3
Friendly Name: soft.lissi.ru
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: PKCS #1 SHA-1 With RSA Encryption
Issuer: "CN=CA-RSA"
Validity:
Not Before: Wed May 20 16:12:00 2020
Not After : Tue May 21 16:12:00 2030
Subject: "CN=CA-RSA"
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
a3:ca:c1:3b:ac:17:1b:32:69:90:8c:70:3b:95:3e:78:
4c:90:55:27:2a:25:05:16:54:d3:88:69:b0:43:a0:20:
3d:ca:0d:a2:f9:a5:2f:8c:e1:69:b6:df:79:bd:25:7d:
aa:71:2b:f2:9f:82:f1:e7:49:cf:fa:3c:b6:6f:80:09:
b2:ee:d5:18:e3:3d:96:67:38:cb:9c:e8:e5:76:c4:a8:
0b:b9:ad:dd:42:25:c7:da:cf:d4:15:41:bf:b0:0e:4f:
d1:9c:b7:d0:b1:32:a0:c7:14:67:ba:a2:9a:e7:23:26:
d7:7e:32:d9:5d:15:47:9e:4b:b0:b1:8b:04:38:1e:c3:
b2:fc:17:fe:8e:d1:cb:de:de:fd:13:17:b3:0e:5b:58:
e1:37:c7:12:32:b6:94:82:77:b8:4c:87:99:c6:c3:7d:
51:ed:3c:41:73:31:aa:13:de:26:84:e7:f7:a9:34:e9:
b3:9e:7d:aa:91:65:79:a7:14:9d:fc:45:42:de:e6:43:
9d:67:96:94:66:38:0b:2e:32:0a:4d:c3:3d:14:b9:06:
6b:e0:92:e2:35:0c:8f:78:7f:2c:ad:ec:dc:67:66:0b:
8c:47:82:c5:0e:39:a5:35:75:b5:fb:7f:2d:07:97:ef:
15:d8:fc:d4:72:6a:da:32:86:9e:64:ea:4a:e3:37:5b
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is a CA with no maximum path length.
Name: Certificate Key Usage
Usages: Certificate Signing
CRL Signing
Name: Certificate Type
Data: <SSL CA,S/MIME CA,ObjectSigning CA>
Name: Certificate Comment
Comment: "xca certificate"
Signature Algorithm: PKCS #1 SHA-1 With RSA Encryption
Signature:
24:90:ac:91:3f:13:f6:1a:d4:3c:1b:de:33:e1:4a:0c:
d8:27:a0:00:d2:43:c8:1b:13:90:93:d3:d2:f0:fe:79:
da:14:fd:34:2e:3a:f4:fc:c8:71:c9:4f:0d:65:c0:fd:
40:04:92:ef:7e:72:35:09:4a:08:1e:ed:21:53:06:03:
73:f9:13:e7:a3:9c:e2:17:9c:25:b2:a5:f9:dc:07:7d:
32:9f:cd:82:85:6c:26:79:dd:ee:e7:31:4e:10:55:19:
d6:ac:1e:70:39:01:d2:37:00:3b:41:de:a9:c2:bd:bf:
b4:c1:f8:8d:bd:d4:6b:95:6d:53:f3:17:76:40:d4:05:
a4:1e:69:e8:54:92:91:bf:89:b6:ba:45:c5:14:89:bb:
f4:44:cf:91:ca:16:44:55:86:8f:b9:37:4e:9e:9e:04:
cd:48:e7:57:ec:c8:e2:72:f3:df:34:49:0a:9b:3f:67:
a4:01:dd:f3:a3:bb:ec:b5:b8:20:f5:7e:45:8e:ae:53:
7e:b8:92:38:0a:b7:41:8e:81:15:ab:72:42:f7:37:4a:
6d:d7:4f:aa:0a:99:ee:9b:49:16:54:03:42:d6:fe:c1:
ee:63:71:28:b1:84:c2:e6:d4:7b:f6:10:4c:a0:7a:39:
9d:03:30:ff:78:24:ce:5b:ac:fe:ac:6d:f6:61:77:a6
Fingerprint (SHA-256):
AA:1F:B9:29:D2:F9:CC:AB:3D:F7:8C:26:26:4B:51:A3:71:01:1A:94:F8:FE:47:1D:BD:E3:72:DD:63:17:FE:6C
Fingerprint (SHA1):
B3:7A:A1:65:01:E2:A0:09:F4:55:17:EC:40:88:5C:42:9A:45:F5:36
Key(shrouded):
Friendly Name: soft.lissi.ru
Encryption algorithm: PKCS #12 V2 PBE With SHA-1 And 3KEY Triple DES-CBC
Parameters:
Salt:
08:0b:8d:be:fa:fc:a5:a3
Iteration Count: 2048 (0x800)
$该实用程序很方便,但并非难事。美中不足的是俄文字母或UTF-8编码显示为点(...)。而且,如果pp实用程序具有-u参数(存在utf-8编码),则他们在这里忘记了它(我们在考虑certutil实用程序时将再次遇到此问题)。解决这个问题并不难:在文件pk12util.c中的函数P12U_ListPKCS12File中添加一行就足够了:
PRIntn
P12U_ListPKCS12File(char *in_file, PK11SlotInfo *slot,
secuPWData *slotPw, secuPWData *p12FilePw)
{
SEC_PKCS12DecoderContext *p12dcx = NULL;
SECItem uniPwitem = { 0 };
SECStatus rv = SECFailure;
const SEC_PKCS12DecoderItem *dip;
/* UTF-8*/
SECU_EnableUtf8Display(PR_TRUE);
. . . . .
}
之后,俄语字母将没有问题。
$ pk12util -l 1000.p12 -d "." -W 01234567
Certificate(has private key):
Data:
Version: 3 (0x2)
Serial Number: 4096 (0x1000)
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Validity:
Not Before: Tue Jul 07 08:40:14 2020
Not After: Fri Aug 06 08:40:14 2021
Subject: «E=test@rsa.ru,CN= »
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
9a:9f:6c:60:94:f7:ec:f7:94:b3:51:01:e2:1a:c5:25:
28:bb:02:77:49:52:4d:99:8a:6e:26:12:55:8f:71:34:
04:da:39:24:f9:b4:6b:d0:0a:42:27:1b:b2:d7:9b:d9:
c3:76:b0:e0:1c:7c:21:ce:79:9f:d5:2b:17:63:cb:94:
5b:d9:b2:53:ff:b9:bf:4f:3d:cf:b7:8d:8a:37:ba:02:
8c:da:d2:0d:fd:46:5b:45:1d:95:64:07:6e:fa:88:0d:
a4:bd:b3:4a:ed:99:f1:fd:73:c5:b6:05:a0:e5:ee:6b:
c3:83:5b:d0:64:05:77:6a:18:d8:c8:28:a1:d0:06:41:
23:0d:bb:87:8a:77:14:fb:6c:5d:af:db:2b:0b:11:a3:
16:1b:2b:05:18:26:a9:b5:00:4a:40:da:b3:05:aa:2a:
67:c0:18:0d:03:f7:d2:b9:ba:7c:36:f9:95:2e:56:81:
a3:09:99:5e:20:10:95:38:10:c9:c1:6f:c3:6c:a6:1b:
78:51:c6:e4:4f:11:bc:c0:22:4b:ca:59:16:f2:45:95:
0d:fd:7b:46:cf:c7:ac:1c:3d:d7:26:fc:ad:80:3e:2c:
21:93:29:32:a6:79:e2:a8:c6:e9:5e:45:34:d3:38:57:
8f:cd:95:5e:91:09:84:34:21:d2:16:29:69:75:4d:a3
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is not a CA.
Name: Certificate Key Usage
Usages: Digital Signature
Key Encipherment
Key Agreement
Name: Certificate Type
Data: <SSL Client,S/MIME>
Name: Extended Key Usage
TLS Web Client Authentication Certificate
E-Mail Protection Certificate
Name: Certificate Subject Key ID
Data:
26:a1:b3:98:1c:fe:62:ba:23:81:96:37:3f:08:bd:70:
d6:f2:b1:46
Name: Certificate Authority Key Identifier
Key ID:
0a:b6:f6:87:64:1d:8e:b3:63:08:29:9f:21:59:ad:47:
d8:ea:07:f4
Issuer:
Directory Name: «E=ca@test.ru,OGRN=1111111111111,INN=22222222
2222,CN= ,OU=
,O=
,STREET=».
, . 0",L=,ST=
,C=RU"
Serial Number:
00:a2:9b:22:32:3e:a7:3d:d8
Name: Certificate Subject Alt Name
RFC822 Name: «test@rsa.ru»
Name: Certificate Issuer Alt Name
Error: Parsing extension: Certificate extension value is invalid.
Data: Sequence {
}
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Signature:
2f:75:7e:71:9e:15:5c:97:fe:a2:e1:2a:52:39:56:55:
e0:62:60:bc:5f:6d:c2:b6:ec:cd:8b:10:b3:b1:3f:e5:
d6:d1:5f:a5:fa:61:c1:ce:3e:db:6a:2f:b2:13:46:8d:
67:cf:18:09:61:97:01:45:bc:99:bb:0c:d6:0a:a3:03:
87:0a:8e:10:3a:d5:e3:94:6d:4a:24:fa:c3:40:0b:43:
c2:3b:00:56:06:c4:d2:fc:b2:7e:e9:00:e5:2f:4b:e2:
3a:91:49:ce:f8:c3:60:ec:01:74:d8:1a:3b:af:e6:f6:
91:db:c5:f1:d7:de:be:18:38:47:41:8a:e2:ef:80:91:
10:54:41:ae:55:22:6f:d7:8c:fa:46:b6:b6:2a:ee:6a:
0c:c9:03:18:af:4e:93:6c:61:f3:b4:78:0c:61:93:f1:
d8:1b:00:c3:e5:29:9a:08:0a:f8:31:67:88:3d:c3:88:
7a:60:c0:c4:52:94:25:56:e5:a3:df:7d:58:c5:df:9a:
c7:22:7e:2c:f6:fb:2c:bf:b7:7f:c5:ca:2b:0f:8c:20:
77:b9:1f:e0:62:5a:3d:d4:6f:12:ea:c8:51:67:a5:75:
ad:e9:ac:9e:4e:2e:2d:34:80:e7:d8:64:f6:8f:2f:33:
32:1f:8b:bc:9c:e8:77:4a:ee:7b:84:31:ec:28:e9:70
Fingerprint (SHA-256):
96:F4:A5:FA:6D:8A:F8:7E:A6:10:49:BD:43:34:C1:92:C6:7D:FF:63:41:8E:69:C0:AC:34:6B:CB:63:7B:56:31
Fingerprint (SHA1):
B6:91:9B:C6:7A:45:9C:92:FD:E7:C7:33:00:FA:91:DF:7D:5F:00:21
Friendly Name:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
00:a2:9b:22:32:3e:a7:3d:d8
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Validity:
Not Before: Tue Jul 07 08:08:11 2020
Not After: Fri Jul 05 08:08:11 2030
Subject: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
e7:08:ed:83:08:10:7b:48:56:37:8b:e2:4a:31:1a:7b:
0d:4e:d2:a2:67:d7:04:60:a0:09:db:06:64:21:01:4e:
0d:41:d8:61:15:c6:58:83:66:7e:6b:65:72:0d:2b:c3:
50:26:11:04:82:4b:1a:12:d0:dc:e1:13:1c:76:69:0f:
c2:59:e2:5d:60:6d:fe:8a:48:fa:8b:1e:05:07:34:6d:
8a:e3:76:23:42:9e:7b:64:0b:6a:fb:36:63:31:96:df:
ed:d3:e8:7c:6e:39:d4:7d:da:b8:f4:ec:53:57:60:f1:
d8:a4:3a:3f:3b:4a:63:6c:2a:55:90:21:15:23:4a:37:
21:31:a0:c4:bb:84:0d:96:18:3c:3b:ba:92:e3:e2:17:
56:e5:d9:8c:58:24:8a:a3:53:b6:4f:02:4d:30:a6:0f:
34:ad:20:cf:6f:03:ca:23:1e:d3:15:bc:80:09:d8:1e:
90:07:da:90:a9:34:9e:6e:ed:6b:10:b7:a1:a4:a9:b4:
04:ac:6a:40:d8:00:52:d6:6a:28:f2:8c:c6:84:81:8a:
cd:63:a6:53:82:d2:4e:11:ec:94:81:d7:9c:79:8a:30:
9c:40:75:4d:d9:88:0b:cc:a4:0c:5d:6d:23:a6:ac:56:
8c:49:d9:1f:2b:63:cb:50:fc:a3:e0:3e:35:4e:f4:03
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is a CA with no maximum path length.
Name: Certificate Subject Key ID
Data:
0a:b6:f6:87:64:1d:8e:b3:63:08:29:9f:21:59:ad:47:
d8:ea:07:f4
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Signature:
17:7d:29:dc:4d:6e:4c:99:7a:bc:b2:2a:a5:80:f9:5f:
0c:60:00:2b:f3:f4:ef:19:d7:ed:56:07:5d:24:e1:b3:
f6:43:e2:05:9b:75:ce:cd:cf:27:1e:1c:cd:d8:cc:43:
77:16:04:7e:8a:dd:89:c4:b2:75:ae:f4:84:23:53:18:
fe:be:c5:1d:40:55:aa:91:9f:f5:96:06:5d:07:22:a8:
1c:b9:29:c4:49:2e:75:10:75:22:95:36:16:58:2f:77:
f5:fa:6d:de:c4:67:ca:f3:e1:98:51:b4:ba:b7:2a:7f:
06:db:33:5a:a6:bb:53:57:f4:18:93:16:9c:0e:43:d0:
46:e6:84:55:bb:ff:68:fe:fa:32:d5:23:2a:d5:65:9b:
d9:63:45:6b:53:71:64:dd:da:e1:40:fa:89:30:b1:73:
8b:f8:7c:3c:2f:72:24:ad:e8:5c:07:89:2f:3a:0d:37:
48:29:1f:0d:5f:9e:11:73:56:b8:d9:24:eb:2d:2e:18:
c7:9b:90:62:09:20:61:75:b9:a1:9a:3f:99:34:8e:06:
30:ce:7d:60:42:7d:e0:14:f2:88:f2:41:a0:46:4d:55:
17:d4:c2:15:64:c9:3e:f5:cc:0a:41:f7:c0:d0:94:96:
ea:64:e0:45:3a:e0:a3:d6:22:a9:d1:e3:c4:51:e8:96
Fingerprint (SHA-256):
F5:DF:15:79:5E:1E:41:84:96:8C:8C:CA:37:0C:A6:BB:C3:21:AE:3D:32:42:8C:63:C2:64:BA:0A:74:DC:37:F8
Fingerprint (SHA1):
CF:C6:B9:D4:3C:16:6F:31:91:2A:09:2F:FE:4C:57:89:0F:5A:F1:DB
Friendly Name:
Key(shrouded):
Friendly Name:
Encryption algorithm: PKCS #12 V2 PBE With SHA-1 And 3KEY Triple DES-CBC
Parameters:
Salt:
c4:fa:4a:6a:4f:54:a1:7a
Iteration Count: 2048 (0x800)
$
Certificate(has private key):
Data:
Version: 3 (0x2)
Serial Number: 4096 (0x1000)
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Validity:
Not Before: Tue Jul 07 08:40:14 2020
Not After: Fri Aug 06 08:40:14 2021
Subject: «E=test@rsa.ru,CN= »
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
9a:9f:6c:60:94:f7:ec:f7:94:b3:51:01:e2:1a:c5:25:
28:bb:02:77:49:52:4d:99:8a:6e:26:12:55:8f:71:34:
04:da:39:24:f9:b4:6b:d0:0a:42:27:1b:b2:d7:9b:d9:
c3:76:b0:e0:1c:7c:21:ce:79:9f:d5:2b:17:63:cb:94:
5b:d9:b2:53:ff:b9:bf:4f:3d:cf:b7:8d:8a:37:ba:02:
8c:da:d2:0d:fd:46:5b:45:1d:95:64:07:6e:fa:88:0d:
a4:bd:b3:4a:ed:99:f1:fd:73:c5:b6:05:a0:e5:ee:6b:
c3:83:5b:d0:64:05:77:6a:18:d8:c8:28:a1:d0:06:41:
23:0d:bb:87:8a:77:14:fb:6c:5d:af:db:2b:0b:11:a3:
16:1b:2b:05:18:26:a9:b5:00:4a:40:da:b3:05:aa:2a:
67:c0:18:0d:03:f7:d2:b9:ba:7c:36:f9:95:2e:56:81:
a3:09:99:5e:20:10:95:38:10:c9:c1:6f:c3:6c:a6:1b:
78:51:c6:e4:4f:11:bc:c0:22:4b:ca:59:16:f2:45:95:
0d:fd:7b:46:cf:c7:ac:1c:3d:d7:26:fc:ad:80:3e:2c:
21:93:29:32:a6:79:e2:a8:c6:e9:5e:45:34:d3:38:57:
8f:cd:95:5e:91:09:84:34:21:d2:16:29:69:75:4d:a3
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is not a CA.
Name: Certificate Key Usage
Usages: Digital Signature
Key Encipherment
Key Agreement
Name: Certificate Type
Data: <SSL Client,S/MIME>
Name: Extended Key Usage
TLS Web Client Authentication Certificate
E-Mail Protection Certificate
Name: Certificate Subject Key ID
Data:
26:a1:b3:98:1c:fe:62:ba:23:81:96:37:3f:08:bd:70:
d6:f2:b1:46
Name: Certificate Authority Key Identifier
Key ID:
0a:b6:f6:87:64:1d:8e:b3:63:08:29:9f:21:59:ad:47:
d8:ea:07:f4
Issuer:
Directory Name: «E=ca@test.ru,OGRN=1111111111111,INN=22222222
2222,CN= ,OU=
,O=
,STREET=».
, . 0",L=,ST=
,C=RU"
Serial Number:
00:a2:9b:22:32:3e:a7:3d:d8
Name: Certificate Subject Alt Name
RFC822 Name: «test@rsa.ru»
Name: Certificate Issuer Alt Name
Error: Parsing extension: Certificate extension value is invalid.
Data: Sequence {
}
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Signature:
2f:75:7e:71:9e:15:5c:97:fe:a2:e1:2a:52:39:56:55:
e0:62:60:bc:5f:6d:c2:b6:ec:cd:8b:10:b3:b1:3f:e5:
d6:d1:5f:a5:fa:61:c1:ce:3e:db:6a:2f:b2:13:46:8d:
67:cf:18:09:61:97:01:45:bc:99:bb:0c:d6:0a:a3:03:
87:0a:8e:10:3a:d5:e3:94:6d:4a:24:fa:c3:40:0b:43:
c2:3b:00:56:06:c4:d2:fc:b2:7e:e9:00:e5:2f:4b:e2:
3a:91:49:ce:f8:c3:60:ec:01:74:d8:1a:3b:af:e6:f6:
91:db:c5:f1:d7:de:be:18:38:47:41:8a:e2:ef:80:91:
10:54:41:ae:55:22:6f:d7:8c:fa:46:b6:b6:2a:ee:6a:
0c:c9:03:18:af:4e:93:6c:61:f3:b4:78:0c:61:93:f1:
d8:1b:00:c3:e5:29:9a:08:0a:f8:31:67:88:3d:c3:88:
7a:60:c0:c4:52:94:25:56:e5:a3:df:7d:58:c5:df:9a:
c7:22:7e:2c:f6:fb:2c:bf:b7:7f:c5:ca:2b:0f:8c:20:
77:b9:1f:e0:62:5a:3d:d4:6f:12:ea:c8:51:67:a5:75:
ad:e9:ac:9e:4e:2e:2d:34:80:e7:d8:64:f6:8f:2f:33:
32:1f:8b:bc:9c:e8:77:4a:ee:7b:84:31:ec:28:e9:70
Fingerprint (SHA-256):
96:F4:A5:FA:6D:8A:F8:7E:A6:10:49:BD:43:34:C1:92:C6:7D:FF:63:41:8E:69:C0:AC:34:6B:CB:63:7B:56:31
Fingerprint (SHA1):
B6:91:9B:C6:7A:45:9C:92:FD:E7:C7:33:00:FA:91:DF:7D:5F:00:21
Friendly Name:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
00:a2:9b:22:32:3e:a7:3d:d8
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Validity:
Not Before: Tue Jul 07 08:08:11 2020
Not After: Fri Jul 05 08:08:11 2030
Subject: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
e7:08:ed:83:08:10:7b:48:56:37:8b:e2:4a:31:1a:7b:
0d:4e:d2:a2:67:d7:04:60:a0:09:db:06:64:21:01:4e:
0d:41:d8:61:15:c6:58:83:66:7e:6b:65:72:0d:2b:c3:
50:26:11:04:82:4b:1a:12:d0:dc:e1:13:1c:76:69:0f:
c2:59:e2:5d:60:6d:fe:8a:48:fa:8b:1e:05:07:34:6d:
8a:e3:76:23:42:9e:7b:64:0b:6a:fb:36:63:31:96:df:
ed:d3:e8:7c:6e:39:d4:7d:da:b8:f4:ec:53:57:60:f1:
d8:a4:3a:3f:3b:4a:63:6c:2a:55:90:21:15:23:4a:37:
21:31:a0:c4:bb:84:0d:96:18:3c:3b:ba:92:e3:e2:17:
56:e5:d9:8c:58:24:8a:a3:53:b6:4f:02:4d:30:a6:0f:
34:ad:20:cf:6f:03:ca:23:1e:d3:15:bc:80:09:d8:1e:
90:07:da:90:a9:34:9e:6e:ed:6b:10:b7:a1:a4:a9:b4:
04:ac:6a:40:d8:00:52:d6:6a:28:f2:8c:c6:84:81:8a:
cd:63:a6:53:82:d2:4e:11:ec:94:81:d7:9c:79:8a:30:
9c:40:75:4d:d9:88:0b:cc:a4:0c:5d:6d:23:a6:ac:56:
8c:49:d9:1f:2b:63:cb:50:fc:a3:e0:3e:35:4e:f4:03
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is a CA with no maximum path length.
Name: Certificate Subject Key ID
Data:
0a:b6:f6:87:64:1d:8e:b3:63:08:29:9f:21:59:ad:47:
d8:ea:07:f4
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Signature:
17:7d:29:dc:4d:6e:4c:99:7a:bc:b2:2a:a5:80:f9:5f:
0c:60:00:2b:f3:f4:ef:19:d7:ed:56:07:5d:24:e1:b3:
f6:43:e2:05:9b:75:ce:cd:cf:27:1e:1c:cd:d8:cc:43:
77:16:04:7e:8a:dd:89:c4:b2:75:ae:f4:84:23:53:18:
fe:be:c5:1d:40:55:aa:91:9f:f5:96:06:5d:07:22:a8:
1c:b9:29:c4:49:2e:75:10:75:22:95:36:16:58:2f:77:
f5:fa:6d:de:c4:67:ca:f3:e1:98:51:b4:ba:b7:2a:7f:
06:db:33:5a:a6:bb:53:57:f4:18:93:16:9c:0e:43:d0:
46:e6:84:55:bb:ff:68:fe:fa:32:d5:23:2a:d5:65:9b:
d9:63:45:6b:53:71:64:dd:da:e1:40:fa:89:30:b1:73:
8b:f8:7c:3c:2f:72:24:ad:e8:5c:07:89:2f:3a:0d:37:
48:29:1f:0d:5f:9e:11:73:56:b8:d9:24:eb:2d:2e:18:
c7:9b:90:62:09:20:61:75:b9:a1:9a:3f:99:34:8e:06:
30:ce:7d:60:42:7d:e0:14:f2:88:f2:41:a0:46:4d:55:
17:d4:c2:15:64:c9:3e:f5:cc:0a:41:f7:c0:d0:94:96:
ea:64:e0:45:3a:e0:a3:d6:22:a9:d1:e3:c4:51:e8:96
Fingerprint (SHA-256):
F5:DF:15:79:5E:1E:41:84:96:8C:8C:CA:37:0C:A6:BB:C3:21:AE:3D:32:42:8C:63:C2:64:BA:0A:74:DC:37:F8
Fingerprint (SHA1):
CF:C6:B9:D4:3C:16:6F:31:91:2A:09:2F:FE:4C:57:89:0F:5A:F1:DB
Friendly Name:
Key(shrouded):
Friendly Name:
Encryption algorithm: PKCS #12 V2 PBE With SHA-1 And 3KEY Triple DES-CBC
Parameters:
Salt:
c4:fa:4a:6a:4f:54:a1:7a
Iteration Count: 2048 (0x800)
$
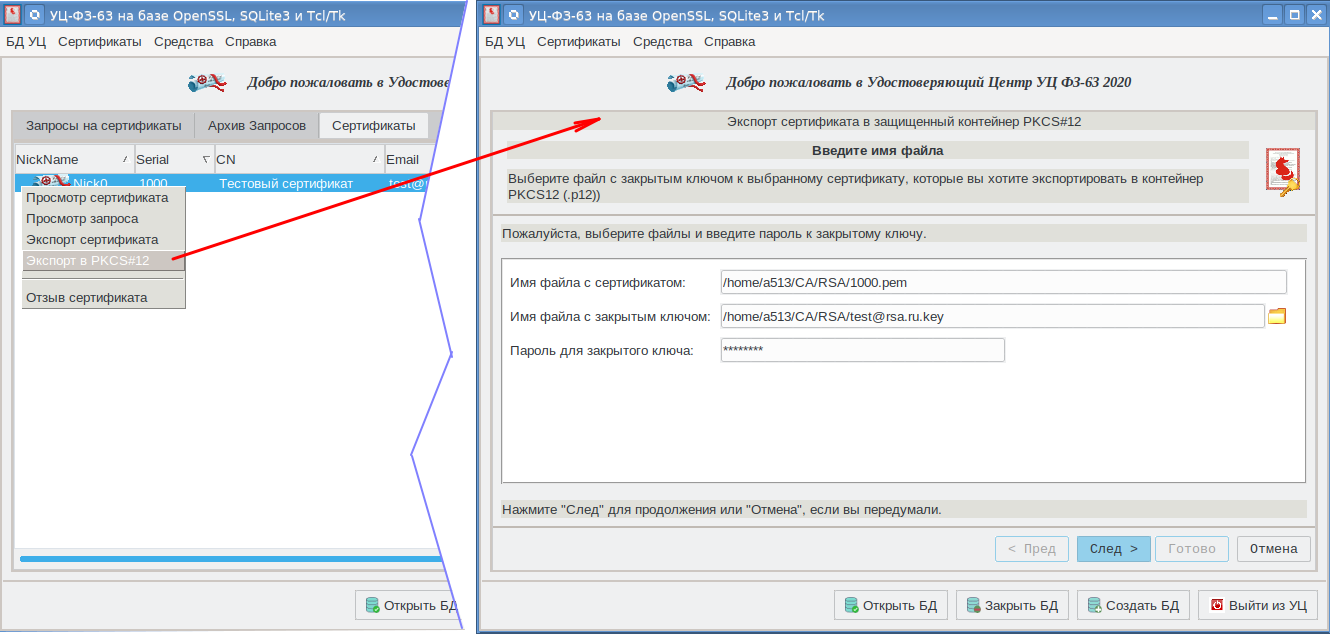
当使用openssl创建PKCS#12容器时,我们使用了CAFL63图形外壳:
现在该讨论NSS存储库了。
NSS储存
NSS存储库是存储三个数据库的目录。
数据库(DB)cert8.db / cert9.db存储证书。 key3.db / key4.db数据库存储私钥。最后,secmod.db / pkcs11.txt数据库存储信息(主要是库的路径),该信息使您可以使用PKCS#11接口使用第三方令牌/智能卡/云。
modutil实用程序旨在创建以下格式的NSS存储库:
modutil -create -force [-dbdir < NSS>] ,
< NSS> := [< >:]< NSS>
< > := dbm|sql , :
$modutil -create -force -dbdir "sql:/~/TEST_NSS"
dbm数据库类型假定创建了伯克利数据库(cert8.db,key3.db和secmod.db)。sql类型假定创建SQLite3数据库(cert9.db,key9.db和文本文件pkcs11.txt)。SQLite3数据库是默认创建的。必须预先创建NSS存储库目录。默认情况下(除非指定了-dbdir或-d参数),将使用用户主文件夹中的“ .netscape”存储。该存储空间例如由google-chrome浏览器使用。
从旧格式(DBM)证书存储区(cert8.db,key3.db和secmod.db)创建新格式(SQLite3)(cert9.db,key4.db和pkcs11.txt)的存储区也很容易。为此,只需以查看密钥(-K)或使用-X参数的证书(-L)的方式运行用于处理证书certutil的实用程序,例如:
$certutil -K -X -d ~/TEST_NSS要么
$certutil -L -X -d ~/TEST_NSS请注意,此类存储库在基于NSS的所有项目中都可用,包括Firefox,Thunderbird,Seamonkey,GoogleChrome和LibreOffice。
创建NSS存储后,带有两个内置令牌的内置“ NSS内部PKCS#11模块”将自动可用:
$modutil -list -dbdir ~/TEST_NSS
Listing of PKCS #11 Modules
-----------------------------------------------------------
1. NSS Internal PKCS #11 Module
uri: pkcs11:library-manufacturer=Mozilla%20Foundation;library-description=NSS%20Internal%20Crypto%20Services;library-version=3.52
slots: 2 slots attached
status: loaded
slot: NSS Internal Cryptographic Services
token: NSS Generic Crypto Services
uri: pkcs11:token=NSS%20Generic%20Crypto%20Services;manufacturer=Mozilla%20Foundation;serial=0000000000000000;model=NSS%203
slot: NSS User Private Key and Certificate Services
token: NSS Certificate DB
uri: pkcs11:token=NSS%20Certificate%20DB;manufacturer=Mozilla%20Foundation;serial=0000000000000000;model=NSS%203
-----------------------------------------------------------
$
“ NSS通用加密服务”令牌实现了加密功能和机制,“ NSS证书数据库”令牌旨在存储证书和密钥以及其他附加信息(例如,有关信任根证书的信息)。“ NSS证书数据库”令牌(内部NSS令牌)使用cert8.db / cert9.db数据库存储证书,并将私钥存储在key3.db / key4.db数据库中。
通过运行以下命令,您可以获取有关NSS Internal PKCS#11模块的内置令牌的信息,包括默认情况下支持的加密机制:
$ modutil -list'NSS内部PKCS#11模块'-dbdir〜/ TEST_NSS
— Name: NSS Internal PKCS #11 Module
Library file: **Internal ONLY module**
Manufacturer: Mozilla Foundation
Description: NSS Internal Crypto Services
PKCS #11 Version 3.0
Library Version: 3.52
Cipher Enable Flags: None
Default Mechanism Flags: RSA:ECC:DH:RC2:RC4:DES:AES:CAMELLIA:SEED:SHA1:SHA256:SHA512:MD5:MD2:SSL:TLS
Slot: NSS Internal Cryptographic Services
Slot Mechanism Flags: RSA:ECC:DH:RC2:RC4:DES:AES:CAMELLIA:SEED:SHA1:SHA256:SHA512:MD5:MD2:SSL:TLS
Manufacturer: Mozilla Foundation
Type: Software
Version Number: 3.52
Firmware Version: 1.0
Status: Enabled
Token Name: NSS Generic Crypto Services
Token Manufacturer: Mozilla Foundation
Token Model: NSS 3
Token Serial Number: 0000000000000000
Token Version: 4.0
Token Firmware Version: 0.0
Access: Write Protected
Login Type: Public (no login required)
User Pin: NOT Initialized
Slot: NSS User Private Key and Certificate Services
Slot Mechanism Flags: None
Manufacturer: Mozilla Foundation
Type: Software
Version Number: 3.52
Firmware Version: 1.0
Status: Enabled
Token Name: NSS Certificate DB
Token Manufacturer: Mozilla Foundation
Token Model: NSS 3
Token Serial Number: 0000000000000000
Token Version: 0.0
Token Firmware Version: 0.0
Access: NOT Write Protected
Login Type: Public (no login required)
User Pin: Initialized
— $
Library file: **Internal ONLY module**
Manufacturer: Mozilla Foundation
Description: NSS Internal Crypto Services
PKCS #11 Version 3.0
Library Version: 3.52
Cipher Enable Flags: None
Default Mechanism Flags: RSA:ECC:DH:RC2:RC4:DES:AES:CAMELLIA:SEED:SHA1:SHA256:SHA512:MD5:MD2:SSL:TLS
Slot: NSS Internal Cryptographic Services
Slot Mechanism Flags: RSA:ECC:DH:RC2:RC4:DES:AES:CAMELLIA:SEED:SHA1:SHA256:SHA512:MD5:MD2:SSL:TLS
Manufacturer: Mozilla Foundation
Type: Software
Version Number: 3.52
Firmware Version: 1.0
Status: Enabled
Token Name: NSS Generic Crypto Services
Token Manufacturer: Mozilla Foundation
Token Model: NSS 3
Token Serial Number: 0000000000000000
Token Version: 4.0
Token Firmware Version: 0.0
Access: Write Protected
Login Type: Public (no login required)
User Pin: NOT Initialized
Slot: NSS User Private Key and Certificate Services
Slot Mechanism Flags: None
Manufacturer: Mozilla Foundation
Type: Software
Version Number: 3.52
Firmware Version: 1.0
Status: Enabled
Token Name: NSS Certificate DB
Token Manufacturer: Mozilla Foundation
Token Model: NSS 3
Token Serial Number: 0000000000000000
Token Version: 0.0
Token Firmware Version: 0.0
Access: NOT Write Protected
Login Type: Public (no login required)
User Pin: Initialized
— $
用于与外部PKCS#11设备一起使用的附加模块的连接是使用相同的modutil实用程序完成的:
$modutil -add < > -libfile < > [-dbdir < NSS>]例如,要使用支持俄语加密的RUToken令牌,只需运行以下命令:
$modutil -add "ruTokenECP" -libfile /usr/lib64/librtpkcs11ecp_2.0.so -dbdir $HOME/.netscape 要获取支持特定NSS存储库的模块的列表,以及有关每个模块的信息(库,所支持的插槽和连接到它们的令牌的列表),请运行以下命令:
$modutil -list [-dbdir < NSS>]
要获取有关特定模块的已连接令牌的完整信息,您将需要运行以下命令:
$modutil -list < > [-dbdir < NSS>]当我们收到有关内置(内部)NSS令牌的信息时,我们已经使用了它。
而且,如果您可以添加模块,则还可以从数据库中删除该模块:
$modutil -delete < > [-dbdir < NSS>] 访问外部令牌通常受PIN保护。默认情况下,对内置NSS Certificate DB令牌的访问不受密码保护(PIN码)。但是建立它并不难,例如:
$modutil -dbdir $HOME/.netscape -changepw "NSS Certificate DB" 同样,您可以更改外部令牌的PIN码。
现在是继续使用令牌,其机制和对象的时候了。
访问PKCS#11令牌对象
certutil实用程序用于访问PKCS#11令牌的对象(密钥,证书)。请注意,certutil实用程序的功能与openssl实用程序的功能相同。要查看certutil实用程序的功能,只需运行以下命令:
$certutil -H但是现在我们只对访问证书和密钥感兴趣。回想一下,当存储在PKCS#11令牌上时,通常都为这两个令牌分配CKA_ID和CKA_LABEL属性。要查看特定令牌上的证书列表,请运行以下命令:
$certutil -L [-d < NSS>] [-h < >]可以将真实令牌标签或关键字之一(全部或内部)指定为令牌标签。在第一种情况下(全部使用令牌标记),将搜索与NSS存储库连接的所有令牌,在第二种情况下(内部或“ NSS证书数据库”)将查看“ NSS证书数据库”存储库的内部令牌。
例如,要获取标记为“ LS11SW2016”的令牌上的证书列表,其访问模块已在NSS存储库“ / home / a513 / tmp / TEST_NSS”中注册,请运行以下命令:
$ certutil -L -d /home/a513/tmp/TEST_NSS -h "LS11SW2016"
Enter Password or Pin for "LS11SW2016":
Certificate Nickname Trust Attributes
SSL,S/MIME,JAR/XPI
LS11SW2016:TestCA_P11 u,u,u
LS11SW2016:clientnss from CryptoArmPKCS u,u,u
LS11SW2016: u,u,u
LS11SW2016:Thenderbird-60.3.0 from 32 u,u,u
LS11SW2016: from 12_512 u,u,u
LS11SW2016:Text4Key u,u,u
LS11SW2016:KmailKleopatra GnuPG-2001 u,u,u
LS11SW2016:setvernss from CryptoArmPKCS u,u,u
LS11SW2016: from 12_512 u,u,u
LS11SW2016:Test 12 512 u,u,u
LS11SW2016:Kleopatra GnuPG-2001 ,,
$令牌上的证书列表显示在两列中。第一列提供证书的昵称,第二列包含该证书的信任属性。
此外,如果证书在其所位于的令牌上具有私钥,则此列将包含值“ u,u,u”。
如果未设置属性,则该列将包含值“,”。
具有“ u,u,u”个信任属性的证书(它们具有私钥)可以用于身份验证或生成电子签名。
可以为嵌入式“ NSS Certificate DB”令牌上的证书设置其他信任属性值。但是稍后会更多。
NSS中证书的昵称是什么?
<nickname> := [< >:]<CKA_LABEL>对于内部令牌(“ NSS证书数据库”),昵称中的令牌标签可能会丢失。
如果我们考虑PKCS#11令牌的机制,将会看到生成密钥,导入证书和密钥本身的操作不提供设置CKA_ID和CKA_LABEL属性的值。这一切都转移给了应用软件开发人员。但是,如果您使用NSS实用程序来处理令牌,那么事实证明它们可以解决麻烦。
以下命令用于查看私钥列表:
$certutil -K [-d < NSS>] [-h < >]这将打印密钥类型,密钥CKA_ID和CKA_LABEL。
但是回到证书。要以文本形式查看令牌上的证书,只需运行以下命令:
$certutil -L [-d < NSS>] -n <nickname >例如:
certutil -L -d'/ home / a513 / tmp / TEST_NSS'-n'NSS证书DB:测试证书'
$ certutil -L -d "/home/a513/tmp/TEST_NSS" -n «NSS Certificate DB: »
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 4096 (0x1000)
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Validity:
Not Before: Tue Jul 07 08:40:14 2020
Not After: Fri Aug 06 08:40:14 2021
Subject: «E=test@rsa.ru,CN= »
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
9a:9f:6c:60:94:f7:ec:f7:94:b3:51:01:e2:1a:c5:25:
28:bb:02:77:49:52:4d:99:8a:6e:26:12:55:8f:71:34:
04:da:39:24:f9:b4:6b:d0:0a:42:27:1b:b2:d7:9b:d9:
c3:76:b0:e0:1c:7c:21:ce:79:9f:d5:2b:17:63:cb:94:
5b:d9:b2:53:ff:b9:bf:4f:3d:cf:b7:8d:8a:37:ba:02:
8c:da:d2:0d:fd:46:5b:45:1d:95:64:07:6e:fa:88:0d:
a4:bd:b3:4a:ed:99:f1:fd:73:c5:b6:05:a0:e5:ee:6b:
c3:83:5b:d0:64:05:77:6a:18:d8:c8:28:a1:d0:06:41:
23:0d:bb:87:8a:77:14:fb:6c:5d:af:db:2b:0b:11:a3:
16:1b:2b:05:18:26:a9:b5:00:4a:40:da:b3:05:aa:2a:
67:c0:18:0d:03:f7:d2:b9:ba:7c:36:f9:95:2e:56:81:
a3:09:99:5e:20:10:95:38:10:c9:c1:6f:c3:6c:a6:1b:
78:51:c6:e4:4f:11:bc:c0:22:4b:ca:59:16:f2:45:95:
0d:fd:7b:46:cf:c7:ac:1c:3d:d7:26:fc:ad:80:3e:2c:
21:93:29:32:a6:79:e2:a8:c6:e9:5e:45:34:d3:38:57:
8f:cd:95:5e:91:09:84:34:21:d2:16:29:69:75:4d:a3
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is not a CA.
Name: Certificate Key Usage
Usages: Digital Signature
Key Encipherment
Key Agreement
Name: Certificate Type
Data: <SSL Client,S/MIME>
Name: Extended Key Usage
TLS Web Client Authentication Certificate
E-Mail Protection Certificate
Name: Certificate Subject Key ID
Data:
26:a1:b3:98:1c:fe:62:ba:23:81:96:37:3f:08:bd:70:
d6:f2:b1:46
Name: Certificate Authority Key Identifier
Key ID:
0a:b6:f6:87:64:1d:8e:b3:63:08:29:9f:21:59:ad:47:
d8:ea:07:f4
Issuer:
Directory Name: «E=ca@test.ru,OGRN=1111111111111,INN=22222222
2222,CN= ,OU=
,O=
,STREET=».
, . 0",L=,ST=
,C=RU"
Serial Number:
00:a2:9b:22:32:3e:a7:3d:d8
Name: Certificate Subject Alt Name
RFC822 Name: «test@rsa.ru»
Name: Certificate Issuer Alt Name
Error: Parsing extension: Certificate extension value is invalid.
Data: Sequence {
}
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Signature:
2f:75:7e:71:9e:15:5c:97:fe:a2:e1:2a:52:39:56:55:
e0:62:60:bc:5f:6d:c2:b6:ec:cd:8b:10:b3:b1:3f:e5:
d6:d1:5f:a5:fa:61:c1:ce:3e:db:6a:2f:b2:13:46:8d:
67:cf:18:09:61:97:01:45:bc:99:bb:0c:d6:0a:a3:03:
87:0a:8e:10:3a:d5:e3:94:6d:4a:24:fa:c3:40:0b:43:
c2:3b:00:56:06:c4:d2:fc:b2:7e:e9:00:e5:2f:4b:e2:
3a:91:49:ce:f8:c3:60:ec:01:74:d8:1a:3b:af:e6:f6:
91:db:c5:f1:d7:de:be:18:38:47:41:8a:e2:ef:80:91:
10:54:41:ae:55:22:6f:d7:8c:fa:46:b6:b6:2a:ee:6a:
0c:c9:03:18:af:4e:93:6c:61:f3:b4:78:0c:61:93:f1:
d8:1b:00:c3:e5:29:9a:08:0a:f8:31:67:88:3d:c3:88:
7a:60:c0:c4:52:94:25:56:e5:a3:df:7d:58:c5:df:9a:
c7:22:7e:2c:f6:fb:2c:bf:b7:7f:c5:ca:2b:0f:8c:20:
77:b9:1f:e0:62:5a:3d:d4:6f:12:ea:c8:51:67:a5:75:
ad:e9:ac:9e:4e:2e:2d:34:80:e7:d8:64:f6:8f:2f:33:
32:1f:8b:bc:9c:e8:77:4a:ee:7b:84:31:ec:28:e9:70
Fingerprint (SHA-256):
96:F4:A5:FA:6D:8A:F8:7E:A6:10:49:BD:43:34:C1:92:C6:7D:FF:63:41:8E:69:C0:AC:34:6B:CB:63:7B:56:31
Fingerprint (SHA1):
B6:91:9B:C6:7A:45:9C:92:FD:E7:C7:33:00:FA:91:DF:7D:5F:00:21
Mozilla-CA-Policy: false (attribute missing)
Certificate Trust Flags:
SSL Flags:
User
Email Flags:
User
Object Signing Flags:
User
$
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 4096 (0x1000)
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: «E=ca@test.ru,OGRN=1111111111111,INN=222222222222,CN=
,OU=
,O= ,STR
EET=». , . 0",L=,ST=
,C=RU"
Validity:
Not Before: Tue Jul 07 08:40:14 2020
Not After: Fri Aug 06 08:40:14 2021
Subject: «E=test@rsa.ru,CN= »
Subject Public Key Info:
Public Key Algorithm: PKCS #1 RSA Encryption
RSA Public Key:
Modulus:
9a:9f:6c:60:94:f7:ec:f7:94:b3:51:01:e2:1a:c5:25:
28:bb:02:77:49:52:4d:99:8a:6e:26:12:55:8f:71:34:
04:da:39:24:f9:b4:6b:d0:0a:42:27:1b:b2:d7:9b:d9:
c3:76:b0:e0:1c:7c:21:ce:79:9f:d5:2b:17:63:cb:94:
5b:d9:b2:53:ff:b9:bf:4f:3d:cf:b7:8d:8a:37:ba:02:
8c:da:d2:0d:fd:46:5b:45:1d:95:64:07:6e:fa:88:0d:
a4:bd:b3:4a:ed:99:f1:fd:73:c5:b6:05:a0:e5:ee:6b:
c3:83:5b:d0:64:05:77:6a:18:d8:c8:28:a1:d0:06:41:
23:0d:bb:87:8a:77:14:fb:6c:5d:af:db:2b:0b:11:a3:
16:1b:2b:05:18:26:a9:b5:00:4a:40:da:b3:05:aa:2a:
67:c0:18:0d:03:f7:d2:b9:ba:7c:36:f9:95:2e:56:81:
a3:09:99:5e:20:10:95:38:10:c9:c1:6f:c3:6c:a6:1b:
78:51:c6:e4:4f:11:bc:c0:22:4b:ca:59:16:f2:45:95:
0d:fd:7b:46:cf:c7:ac:1c:3d:d7:26:fc:ad:80:3e:2c:
21:93:29:32:a6:79:e2:a8:c6:e9:5e:45:34:d3:38:57:
8f:cd:95:5e:91:09:84:34:21:d2:16:29:69:75:4d:a3
Exponent: 65537 (0x10001)
Signed Extensions:
Name: Certificate Basic Constraints
Critical: True
Data: Is not a CA.
Name: Certificate Key Usage
Usages: Digital Signature
Key Encipherment
Key Agreement
Name: Certificate Type
Data: <SSL Client,S/MIME>
Name: Extended Key Usage
TLS Web Client Authentication Certificate
E-Mail Protection Certificate
Name: Certificate Subject Key ID
Data:
26:a1:b3:98:1c:fe:62:ba:23:81:96:37:3f:08:bd:70:
d6:f2:b1:46
Name: Certificate Authority Key Identifier
Key ID:
0a:b6:f6:87:64:1d:8e:b3:63:08:29:9f:21:59:ad:47:
d8:ea:07:f4
Issuer:
Directory Name: «E=ca@test.ru,OGRN=1111111111111,INN=22222222
2222,CN= ,OU=
,O=
,STREET=».
, . 0",L=,ST=
,C=RU"
Serial Number:
00:a2:9b:22:32:3e:a7:3d:d8
Name: Certificate Subject Alt Name
RFC822 Name: «test@rsa.ru»
Name: Certificate Issuer Alt Name
Error: Parsing extension: Certificate extension value is invalid.
Data: Sequence {
}
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Signature:
2f:75:7e:71:9e:15:5c:97:fe:a2:e1:2a:52:39:56:55:
e0:62:60:bc:5f:6d:c2:b6:ec:cd:8b:10:b3:b1:3f:e5:
d6:d1:5f:a5:fa:61:c1:ce:3e:db:6a:2f:b2:13:46:8d:
67:cf:18:09:61:97:01:45:bc:99:bb:0c:d6:0a:a3:03:
87:0a:8e:10:3a:d5:e3:94:6d:4a:24:fa:c3:40:0b:43:
c2:3b:00:56:06:c4:d2:fc:b2:7e:e9:00:e5:2f:4b:e2:
3a:91:49:ce:f8:c3:60:ec:01:74:d8:1a:3b:af:e6:f6:
91:db:c5:f1:d7:de:be:18:38:47:41:8a:e2:ef:80:91:
10:54:41:ae:55:22:6f:d7:8c:fa:46:b6:b6:2a:ee:6a:
0c:c9:03:18:af:4e:93:6c:61:f3:b4:78:0c:61:93:f1:
d8:1b:00:c3:e5:29:9a:08:0a:f8:31:67:88:3d:c3:88:
7a:60:c0:c4:52:94:25:56:e5:a3:df:7d:58:c5:df:9a:
c7:22:7e:2c:f6:fb:2c:bf:b7:7f:c5:ca:2b:0f:8c:20:
77:b9:1f:e0:62:5a:3d:d4:6f:12:ea:c8:51:67:a5:75:
ad:e9:ac:9e:4e:2e:2d:34:80:e7:d8:64:f6:8f:2f:33:
32:1f:8b:bc:9c:e8:77:4a:ee:7b:84:31:ec:28:e9:70
Fingerprint (SHA-256):
96:F4:A5:FA:6D:8A:F8:7E:A6:10:49:BD:43:34:C1:92:C6:7D:FF:63:41:8E:69:C0:AC:34:6B:CB:63:7B:56:31
Fingerprint (SHA1):
B6:91:9B:C6:7A:45:9C:92:FD:E7:C7:33:00:FA:91:DF:7D:5F:00:21
Mozilla-CA-Policy: false (attribute missing)
Certificate Trust Flags:
SSL Flags:
User
Email Flags:
User
Object Signing Flags:
User
$
如果在同一令牌上查看的证书具有私钥,则证书信任标志将为用户:
证书信任标志:
SSL标志:
用户
电子邮件标志:
用户
对象签名标志:
用户
要将证书从令牌导出到标准输出,只需添加其他“ -a”或“ -r”参数。“ -a”选项指示以PEM格式输出证书:
$ certutil -L -d'/ home / a513 / tmp / TEST_NSS'-n'NSS证书DB:测试证书'-a
-----BEGIN CERTIFICATE-----
MIIGiTCCBXGgAwIBAgICEAAwDQYJKoZIhvcNAQELBQAwggF2MQswCQYDVQQGEwJS
VTEsMCoGA1UECAwj0JzQvtGB0LrQvtCy0YHQutCw0Y8g0L7QsdC70LDRgdGC0Ywx
GzAZBgNVBAcMEtCl0LDQsdGA0LDQs9GA0LDQtDEqMCgGA1UECQwh0YPQuy4g0KXQ
sNCy0YDQvtCy0YHQutCw0Y8sINC0LiAwMTAwLgYDVQQKDCfQo9C00L7RgdGC0L7Q
stC10YDRj9GO0YjQuNC5INCm0LXQvdGC0YAxOzA5BgNVBAsMMtCe0YLQtNC10Lsg
0KPQtNC+0YHRgtC+0LLQtdGA0Y/RjtGI0LjQuSDQptC10L3RgtGAMTAwLgYDVQQD
DCfQo9C00L7RgdGC0L7QstC10YDRj9GO0YjQuNC5INCm0LXQvdGC0YAxGjAYBggq
hQMDgQMBARIMMjIyMjIyMjIyMjIyMRgwFgYFKoUDZAESDTExMTExMTExMTExMTEx
GTAXBgkqhkiG9w0BCQEWCmNhQHRlc3QucnUwHhcNMjAwNzA3MDg0MDE0WhcNMjEw
ODA2MDg0MDE0WjBMMS4wLAYDVQQDDCXQotC10YHRgtC+0LLRi9C5INGB0LXRgNGC
0LjRhNC40LrQsNGCMRowGAYJKoZIhvcNAQkBFgt0ZXN0QHJzYS5ydTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBAJqfbGCU9+z3lLNRAeIaxSUouwJ3SVJN
mYpuJhJVj3E0BNo5JPm0a9AKQicbsteb2cN2sOAcfCHOeZ/VKxdjy5Rb2bJT/7m/
Tz3Pt42KN7oCjNrSDf1GW0UdlWQHbvqIDaS9s0rtmfH9c8W2BaDl7mvDg1vQZAV3
ahjYyCih0AZBIw27h4p3FPtsXa/bKwsRoxYbKwUYJqm1AEpA2rMFqipnwBgNA/fS
ubp8NvmVLlaBowmZXiAQlTgQycFvw2ymG3hRxuRPEbzAIkvKWRbyRZUN/XtGz8es
HD3XJvytgD4sIZMpMqZ54qjG6V5FNNM4V4/NlV6RCYQ0IdIWKWl1TaMCAwEAAaOC
AkcwggJDMAwGA1UdEwEB/wQCMAAwCwYDVR0PBAQDAgOoMBEGCWCGSAGG+EIBAQQE
AwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwQwHQYDVR0OBBYEFCah
s5gc/mK6I4GWNz8IvXDW8rFGMIIBsAYDVR0jBIIBpzCCAaOAFAq29odkHY6zYwgp
nyFZrUfY6gf0oYIBfqSCAXowggF2MQswCQYDVQQGEwJSVTEsMCoGA1UECAwj0JzQ
vtGB0LrQvtCy0YHQutCw0Y8g0L7QsdC70LDRgdGC0YwxGzAZBgNVBAcMEtCl0LDQ
sdGA0LDQs9GA0LDQtDEqMCgGA1UECQwh0YPQuy4g0KXQsNCy0YDQvtCy0YHQutCw
0Y8sINC0LiAwMTAwLgYDVQQKDCfQo9C00L7RgdGC0L7QstC10YDRj9GO0YjQuNC5
INCm0LXQvdGC0YAxOzA5BgNVBAsMMtCe0YLQtNC10Lsg0KPQtNC+0YHRgtC+0LLQ
tdGA0Y/RjtGI0LjQuSDQptC10L3RgtGAMTAwLgYDVQQDDCfQo9C00L7RgdGC0L7Q
stC10YDRj9GO0YjQuNC5INCm0LXQvdGC0YAxGjAYBggqhQMDgQMBARIMMjIyMjIy
MjIyMjIyMRgwFgYFKoUDZAESDTExMTExMTExMTExMTExGTAXBgkqhkiG9w0BCQEW
CmNhQHRlc3QucnWCCQCimyIyPqc92DAWBgNVHREEDzANgQt0ZXN0QHJzYS5ydTAJ
BgNVHRIEAjAAMA0GCSqGSIb3DQEBCwUAA4IBAQAvdX5xnhVcl/6i4SpSOVZV4GJg
vF9twrbszYsQs7E/5dbRX6X6YcHOPttqL7ITRo1nzxgJYZcBRbyZuwzWCqMDhwqO
EDrV45RtSiT6w0ALQ8I7AFYGxNL8sn7pAOUvS+I6kUnO+MNg7AF02Bo7r+b2kdvF
8dfevhg4R0GK4u+AkRBUQa5VIm/XjPpGtrYq7moMyQMYr06TbGHztHgMYZPx2BsA
w+UpmggK+DFniD3DiHpgwMRSlCVW5aPffVjF35rHIn4s9vssv7d/xcorD4wgd7kf
4GJaPdRvEurIUWelda3prJ5OLi00gOfYZPaPLzMyH4u8nOh3Su57hDHsKOlw
-----END CERTIFICATE-----
MIIGiTCCBXGgAwIBAgICEAAwDQYJKoZIhvcNAQELBQAwggF2MQswCQYDVQQGEwJS
VTEsMCoGA1UECAwj0JzQvtGB0LrQvtCy0YHQutCw0Y8g0L7QsdC70LDRgdGC0Ywx
GzAZBgNVBAcMEtCl0LDQsdGA0LDQs9GA0LDQtDEqMCgGA1UECQwh0YPQuy4g0KXQ
sNCy0YDQvtCy0YHQutCw0Y8sINC0LiAwMTAwLgYDVQQKDCfQo9C00L7RgdGC0L7Q
stC10YDRj9GO0YjQuNC5INCm0LXQvdGC0YAxOzA5BgNVBAsMMtCe0YLQtNC10Lsg
0KPQtNC+0YHRgtC+0LLQtdGA0Y/RjtGI0LjQuSDQptC10L3RgtGAMTAwLgYDVQQD
DCfQo9C00L7RgdGC0L7QstC10YDRj9GO0YjQuNC5INCm0LXQvdGC0YAxGjAYBggq
hQMDgQMBARIMMjIyMjIyMjIyMjIyMRgwFgYFKoUDZAESDTExMTExMTExMTExMTEx
GTAXBgkqhkiG9w0BCQEWCmNhQHRlc3QucnUwHhcNMjAwNzA3MDg0MDE0WhcNMjEw
ODA2MDg0MDE0WjBMMS4wLAYDVQQDDCXQotC10YHRgtC+0LLRi9C5INGB0LXRgNGC
0LjRhNC40LrQsNGCMRowGAYJKoZIhvcNAQkBFgt0ZXN0QHJzYS5ydTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBAJqfbGCU9+z3lLNRAeIaxSUouwJ3SVJN
mYpuJhJVj3E0BNo5JPm0a9AKQicbsteb2cN2sOAcfCHOeZ/VKxdjy5Rb2bJT/7m/
Tz3Pt42KN7oCjNrSDf1GW0UdlWQHbvqIDaS9s0rtmfH9c8W2BaDl7mvDg1vQZAV3
ahjYyCih0AZBIw27h4p3FPtsXa/bKwsRoxYbKwUYJqm1AEpA2rMFqipnwBgNA/fS
ubp8NvmVLlaBowmZXiAQlTgQycFvw2ymG3hRxuRPEbzAIkvKWRbyRZUN/XtGz8es
HD3XJvytgD4sIZMpMqZ54qjG6V5FNNM4V4/NlV6RCYQ0IdIWKWl1TaMCAwEAAaOC
AkcwggJDMAwGA1UdEwEB/wQCMAAwCwYDVR0PBAQDAgOoMBEGCWCGSAGG+EIBAQQE
AwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwQwHQYDVR0OBBYEFCah
s5gc/mK6I4GWNz8IvXDW8rFGMIIBsAYDVR0jBIIBpzCCAaOAFAq29odkHY6zYwgp
nyFZrUfY6gf0oYIBfqSCAXowggF2MQswCQYDVQQGEwJSVTEsMCoGA1UECAwj0JzQ
vtGB0LrQvtCy0YHQutCw0Y8g0L7QsdC70LDRgdGC0YwxGzAZBgNVBAcMEtCl0LDQ
sdGA0LDQs9GA0LDQtDEqMCgGA1UECQwh0YPQuy4g0KXQsNCy0YDQvtCy0YHQutCw
0Y8sINC0LiAwMTAwLgYDVQQKDCfQo9C00L7RgdGC0L7QstC10YDRj9GO0YjQuNC5
INCm0LXQvdGC0YAxOzA5BgNVBAsMMtCe0YLQtNC10Lsg0KPQtNC+0YHRgtC+0LLQ
tdGA0Y/RjtGI0LjQuSDQptC10L3RgtGAMTAwLgYDVQQDDCfQo9C00L7RgdGC0L7Q
stC10YDRj9GO0YjQuNC5INCm0LXQvdGC0YAxGjAYBggqhQMDgQMBARIMMjIyMjIy
MjIyMjIyMRgwFgYFKoUDZAESDTExMTExMTExMTExMTExGTAXBgkqhkiG9w0BCQEW
CmNhQHRlc3QucnWCCQCimyIyPqc92DAWBgNVHREEDzANgQt0ZXN0QHJzYS5ydTAJ
BgNVHRIEAjAAMA0GCSqGSIb3DQEBCwUAA4IBAQAvdX5xnhVcl/6i4SpSOVZV4GJg
vF9twrbszYsQs7E/5dbRX6X6YcHOPttqL7ITRo1nzxgJYZcBRbyZuwzWCqMDhwqO
EDrV45RtSiT6w0ALQ8I7AFYGxNL8sn7pAOUvS+I6kUnO+MNg7AF02Bo7r+b2kdvF
8dfevhg4R0GK4u+AkRBUQa5VIm/XjPpGtrYq7moMyQMYr06TbGHztHgMYZPx2BsA
w+UpmggK+DFniD3DiHpgwMRSlCVW5aPffVjF35rHIn4s9vssv7d/xcorD4wgd7kf
4GJaPdRvEurIUWelda3prJ5OLi00gOfYZPaPLzMyH4u8nOh3Su57hDHsKOlw
-----END CERTIFICATE-----
对于DER输出,请使用“ -r”参数。
安装令牌的证书
假设您有一个PKCS#12容器,其中包含使用OpenSSL生成的个人证书和私钥。要将个人证书导出到NSS存储,请使用以下pk12util命令:
$pk12util -i < pkcs12> [-d < NSS>] [-h < >]如果要为特定令牌导入证书,则需要设置其标签。让我们注意另一个功能。如果容器包含根证书,则它们将被保存在内部令牌“ NSS证书数据库”中。默认情况下,这不会设置信任属性。如果出于某种原因需要设置某些注册机构证书(根证书)或SSL证书的信任属性,则使用以下形式的certutil实用程序:
$certutil -M -n <nickname-> -t < > [-d < NSS>]对于每个证书,有三种可用的信任类别,以下列顺序表示:SSL,S / MIME,每种信任设置的代码签名:
< > := x,y,z , - x-SSL的属性,
- y-S / MIME的属性,
- z-代码签名的属性。
每个x,y和z位置都可以为空(使用,没有显式信任)或包含一个或多个属性:
- p-有效对等体;
- P-可信节点(表示p)
- c-注册机构的有效证书(有效CA)
- T-用于颁发客户端证书的受信任CA(也暗含c)
- C-颁发服务器证书的受信任CA(仅SSL)(隐含c)
请注意,并非所有外来令牌都允许将私钥导入令牌的操作。
要从文件安装简单证书,请使用以下格式的certutil实用程序:
$certutil -A -n < > -t < > [-d < NSS>] [-h < >] [-a] [-i < >]不幸的是,在这种情况下,<certificate label>不等同于上面讨论的证书昵称。在此,证书标签仅匹配CKA_LABEL,仅标签而不指定令牌标签。某种不一致。
默认情况下,假定证书位于DER编码文件中。如果证书是PEM编码的,则必须指定“ -a”参数。如果未指定“ -i”参数,那么将从标准输入(stdin)中获取证书。默认情况下,证书安装到“ NSS证书数据库”令牌,但是您可以将证书安装到外部令牌(“ -h”参数)。在外部令牌上安装证书时,证书将同时安装在内部令牌(“ NSS证书数据库”)和外部令牌上。在这种情况下,外部令牌的信任属性将被忽略,并发出警告:“无法更改证书的信任”。
如果需要,可以删除内部令牌上的重复证书。
要从任何令牌中删除证书,请使用以下命令:
$certutil -D [-d < NSS>] -n <nickname->例如,要从RuTokenECP20令牌中删除带有标签(CKA_LABEL)“ User1”的证书,只需运行以下命令:
$certutil -D -d /home/a513/tmp/TEST_NSS -n "RuTokenECP20:1"删除证书时,它的私钥不会被删除(当然,如果有的话)。要删除私钥,您需要运行以下命令:
$certutil -F [-k < >] [-d < NSS>] -n <nickname->,
< > := rsa|dsa|ec
现在我们有了NSS信息库,带有个人证书的令牌,我们可以使用电子签名了。
电子签名的形成和验证
NSS软件包中提供了三个用于处理电子签名的实用程序。
p7sign实用程序用于生成电子签名:
$pksign -k <nickname > [-d < NSS>] [-e] [-i < >] [-o < >],
<nickname > := [< >:]<CKA_LABEL>
不幸的是,该实用程序会在不参考其形成时间的情况下生成签名。但这很容易解决。在p7sign.c实用程序的SignFile函数中添加一行,并调用该函数以添加签名生成时间就足够了:
SignFile(FILE *outFile, PRFileDesc *inFile, CERTCertificate *cert,
PRBool encapsulated)
{
. . .
/* XXX Need a better way to handle that usage stuff! */
cinfo = SEC_PKCS7CreateSignedData(cert, certUsageEmailSigner, NULL,
SEC_OID_SHA1,
encapsulated ? NULL : &digest,
NULL, NULL);
if (cinfo == NULL)
return -1;
/* */
SEC_PKCS7AddSigningTime(cinfo);
if (encapsulated) {
SEC_PKCS7SetContent(cinfo, (char *)data2sign.data, data2sign.len);
}
. . .
}现在将以CAdes-BES格式生成电子签名。
在NSS中,可以将证书及其私钥存储在同一令牌上,并且它们的标签(CKA_LABEL)和CKA_ID都相同。因此,私钥的昵称和证书本身的昵称是相同的。回想一下,可以通过查看的证书的信任属性的值“ u,u,u”找到证书中私钥的存在(命令certutil -L)。
默认情况下,p7sign实用程序会生成一个分离的签名。如果需要附加的签名,则必须指定“ -e”参数。应该记住的是,如果在NSS存储中的内部令牌上,没有用于签名者证书的根证书链,或者未设置签名者的信任属性,则不会生成签名。
p7verify实用程序用于验证电子签名:
$p7verify -c < > -s < > [-d < NSS>] [-u < >] “ -u”参数值得关注。它指示检查签名者证书的类型,如果与指定的类型不匹配,则签名无效。
值<证书使用情况>可以具有以下值:
0 - certUsageSSLClient
1 - certUsageSSLServer
2 - certUsageSSLServerWithStepUp
3 - certUsageSSLCA
4 - certUsageEmailSigner
5 - certUsageEmailRecipient
6 - certUsageObjectSigner
7 - certUsageUserCertImport
8 - certUsageVerifyCA
9 - certUsageProtectedObjectSigner
10 - certUsageStatusResponder
11 - certUsageAnyCA
12 - certUsageIPsec
默认值为certUsageEmailSigner(4)。
通过p7content实用程序,您可以获得有关文档签署时间,签名人以及签署者的电子邮件地址的信息。如果附加了签名,则还将检索已签名的内容本身。
p7content实用程序具有以下格式:
$p7content [-d < NSS>] [-i < >] [-o < >]例如:
$ p7content -d "sql:/home/a513/tmp/TEST_NSS" -i "/home/a513/DATE_NSS.txt.p7s"
Content printed between bars (newline added before second bar):
# , "-" ()
#
---------------------------------------------
NSS
---------------------------------------------
Content was not encrypted.
Signature is valid.
The signer's common name is 1
The signer's email address is user1@mail.ru
Signing time: Fri Jul 17 10:00:45 2020
There were certs or crls included.
$这些只是NSS软件包中包含的一些实用程序。当然,OpenSSL和NSS都具有实用程序(或命令),可让您创建证书请求并颁发证书,即可以部署功能齐全的CA,就像使用openssl一样。您可以使用selfserv实用程序(openssl s_server的类似物)提高tls服务器,并使用tls-client tstclnt(openssl s-client的类似物)等等。
顺便说一句,您可以使用listsuites实用程序在NSS中获得一组密码套件。在OpenSSL中,openssl ciphers命令用于此目的。可在此处找到OpenSSL密码套件名称到IANA密码套件名称的映射。
实际上,OpenSSL和NSS是同一事物的两个方面(两种类型的接口,用于相同的协议和标准),即公用密钥基础结构。
如果对此主题感兴趣,那么故事将继续。
最后,我还想谈谈NSS的图形外壳。OpenSSL有各种图形化外壳。我们将提到其中只有两个- XCA和CAFL63。
NSS软件包的Guinsspy GUI
第一个问题是要发展什么?这是用Python决定的。
第二个问题是在什么上面编写图形界面?答案是Tkinter。
gui最初是在PAGE上开发的。但是后来他们离开了他。但是上下文仍然存在。
该实用程序的功能基于上述实用程序和命令。除它们之外,还添加了另一个基于“ certutil -R”命令的功能“创建证书请求”:
决定将python3的Breeze主题和python2的Arc主题用作小部件的主题,因为后者缺少Breeze主题。为此,您需要安装带有主题的pythona软件包:
$pip install ttkthemes我们还需要fsb795软件包来使用证书:
$pip install fsb795guinsspy所基于的NSS实用程序经常通过控制台要求输入密码或PIN。通过GUI与他们进行交互的唯一方法是使用pexpect软件包:
$pip install pexpect作为使用pexpect包的示例,以下是用于导入PKCS#12容器的代码:
进口P12
def importP12(frameManager):
global readpw
global filename
tokname = frameManager.STCombobox1.get()
fp12 = frameManager.SEntry1.get()
if (fp12 == () or fp12 == ''):
tkMessageBox.showinfo(title=" PKCS#12", message=' \n')
return (-1, "", "")
filename = fp12
if sys.platform != "win32":
cmd_import_p12 = '"' + patch_win + 'pk12util" -i "' + fp12 + '" -h "' + tokname + '" -d "' + NSSname + '"'
id = pexpect.spawn(cmd_import_p12, timeout=1)
else:
cmd_import_p12 = '"' + patch_win + 'pk12util" -i "' + fp12 + '" -h "' + tokname + '" -d "' + NSSname + '"'
id = pexpect.popen_spawn.PopenSpawn(cmd_import_p12, timeout=10)
while(True):
ret = id.expect(["Enter Password or Pin", "Enter password for PKCS12 file",pexpect.EOF, pexpect.TIMEOUT])
if (ret == 0 or ret == 1):
root.update()
if (ret == 0):
password('', tokname, 0)
pasP11 = readpw
else:
password('', os.path.basename(fp12), 1)
pasP12 = readpw
if (readpwok == 0):
if sys.platform != "win32":
id.close()
return (-3, fp12, "")
if sys.platform != "win32":
id.send(readpw)
id.send("\r")
else:
id.sendline(readpw)
lseek = 1
elif (ret == 2):
break
elif (ret == 3):
break
if sys.platform != "win32":
id.close()
return (-1, fp12, "")
if sys.platform != "win32":
res = id.before.decode('UTF-8')
id.close()
else:
res = id.before.decode('UTF-8')
if (res.find("PKCS12 IMPORT SUCCESSFUL") != -1):
ret = 0
elif (res.find("SEC_ERROR_BAD_PASSWORD") != -1):
ret = -1
return (ret, fp12, "")
else:
ret = -2
return (ret, fp12, res)过程中的无穷循环(while(True):)等待以下四个事件之一发生:
ret = id.expect(["Enter Password or Pin", "Enter password for PKCS12 file",pexpect.EOF, pexpect.TIMEOUT])第一个事件与输入密码或PIN(“输入密码或PIN”)的邀请相关联。
发生这种情况时,屏幕上将显示一个用于输入PIN码的窗口(屏幕截图中的左窗口):
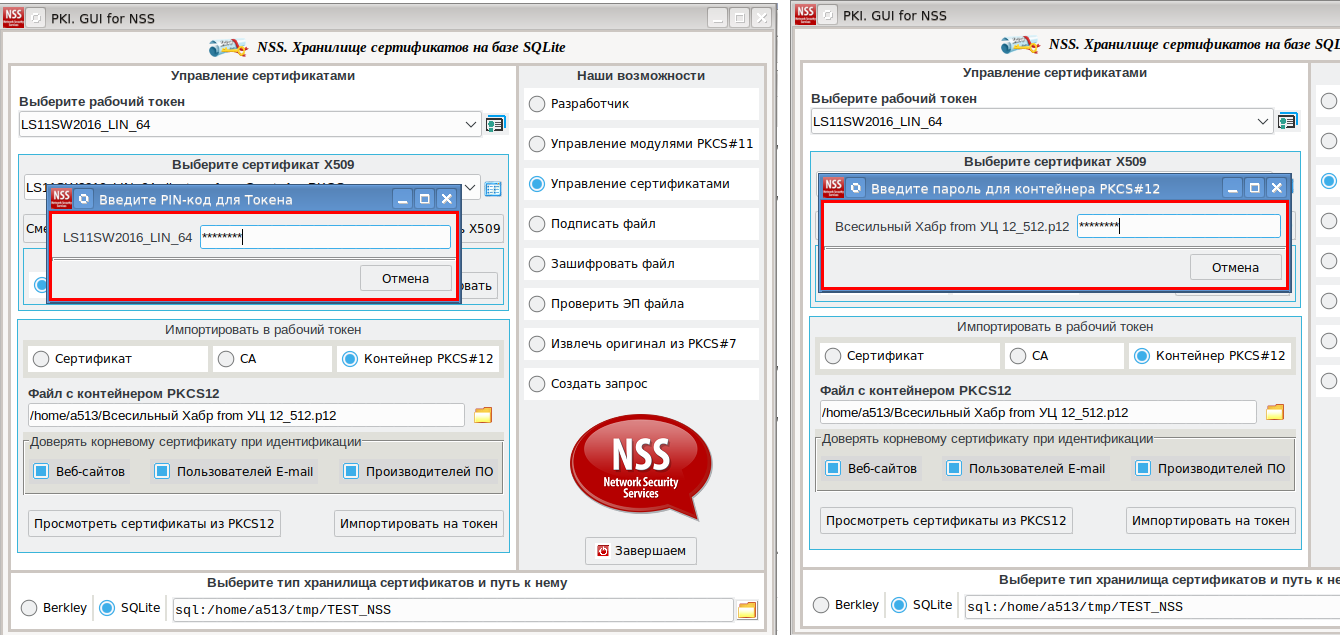
第二个事件与输入PKCS#12容器的密码(“输入PKCS12文件的密码”)相关。发生这种情况时,将在屏幕上显示用于输入带有PKCS#12容器的文件密码的窗口(屏幕截图中的右窗口)。
第三个事件与pk12util实用程序的终止(pexpect.EOF)相关联,而第四个事件与该实用程序的超时终止(pexpect.TIMEOUT)相关联。
guinsspy的源代码可以在这里找到。在此可以找到NSS软件包的分发工具包,该分发工具包可与带有俄罗斯密码的PKCS#11令牌配合使用,用于Linux x86_64平台。
要测试俄语加密令牌,请将NSS_GOST_3.52.1_Linux_x86_64文件夹复制到您的主目录中。创建一个guinsspy_gost.sh脚本:
export LD_LIBRARY_PATH=~/NSS_GOST_3.52.1_Linux_x86_64:$LD_LIBRARY_PATH
export PATH=~/NSS_GOST_3.52.1_Linux_x86_64:$PATH
python3 guinsspy.py
现在运行此脚本并使用俄语令牌。
如果您手边没有带有俄罗斯加密技术的令牌,请转到“创建软件/云令牌”标签,该标签将告诉您如何在计算机上创建软件令牌或连接到云令牌:
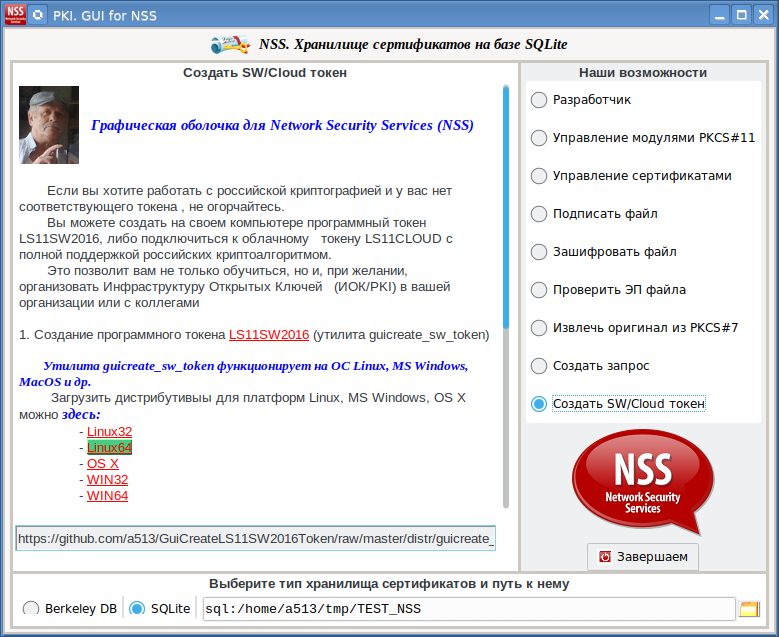
最后,创建证书
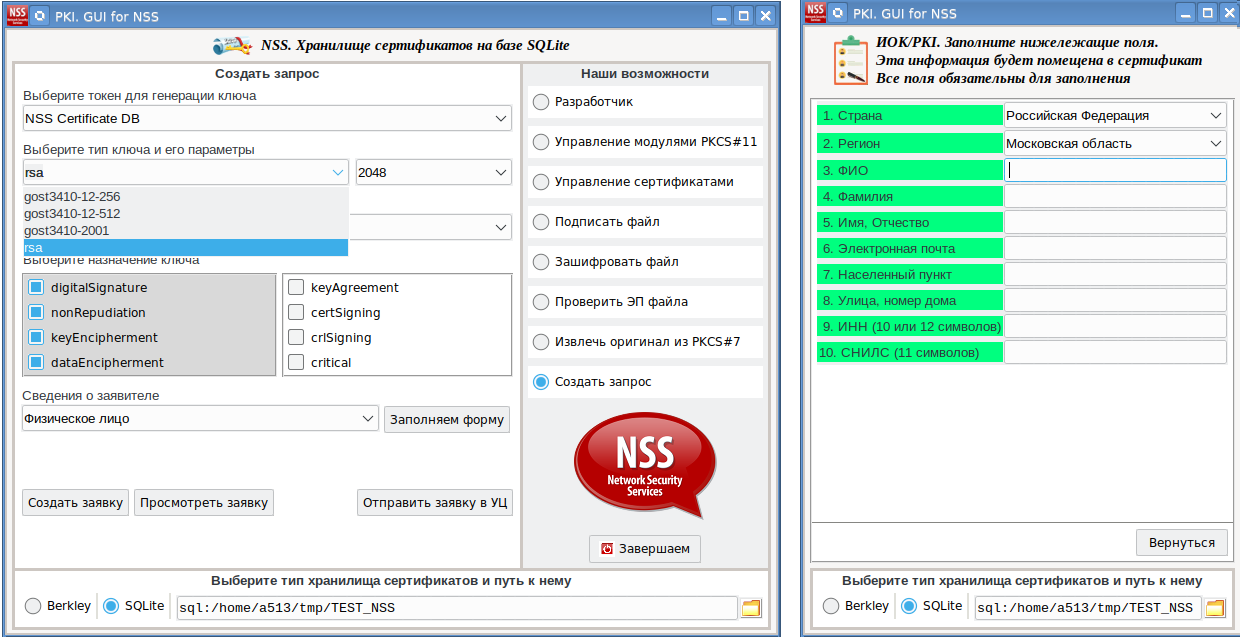
请求的屏幕截图:已收到请求可以将其转移到CAFL63并向其颁发证书,证书安装在创建私钥的令牌上。然后例如使用此证书对文档进行签名。